Introduction:
Hi everyone It’s been a while since my last post but I’m back, I want to tell you a short story about the Microsoft bug bounty program and why you can always check the basic payloads because you will surprise that some times will work:
SPOILER ALERT: I highly recommend Miscrosoft Bug Bounty Program, in my experience their program is much better compared with another big companies programs
This blogpost appeared first in the book Bug Bounty Write Ups Collection
Title: XSS Stored on outlook.com (iOS) via doc file.
Product / URL: outlook.com iOS browser (Google chrome)
Report sent via secure@microsoft.com
Hi Microsoft Security team.
I’ve found a XSS stored in outlook.live.com in iOS browsers via msoffice (ppt) file.
POC:
1.- Create a msoffice document per example a power point presentation with an hyperlink pointing to the url address “javascript:prompt(document.cookie)” and save as “Powerpoint presentation 97-2003 Presentation”, Is very important save the doc as 97-2003, if you don’t save the document as this version the bug reproduction may not work.
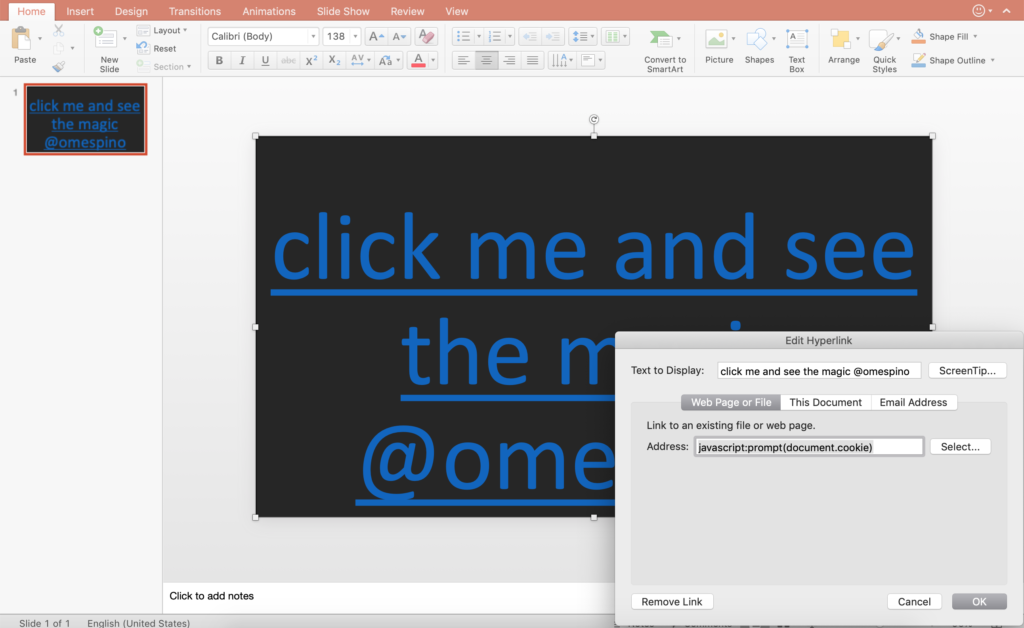
2.- Login in to outlook.live.com (outlook email), upload to msoffice ppt file and send the file via email.
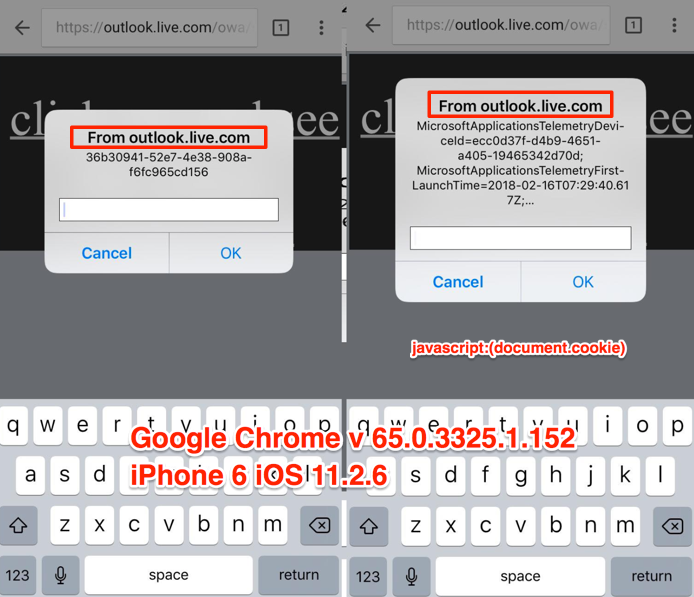
3.- Login into outlook.live.com (outlook email) in Google chrome iOS browser, open the email with the special crafted document, click the attachment and then click download, after that the document ppt will render in Google chrome , then click the hyperlink and see the XSS (shows up the document.cookie).
Something important to highlight is: At this time you have a “magic” link that points directly to the ppt special crafted document.
4 .- Open the link directly in Chrome iOS browser, click the hyperlink, and see the XSS(shows up again the document.cookie) , if you open the link in any iOS browser like Safari, Firefox, Chrome, Opera the XSS works, you just need to be logged in your outlook account, only works in iOS).
Impact
Stored XSS allows an attacker to embed a malicious and arbitraries scripts into a vulnerable page, which is then executed when a victim views the page.
Environment
iPhone 6 – iOS v11.2.5.
Safari Lastest version
Google Chrome Lastest version
My personal email account and all testing was seding emails to myself.
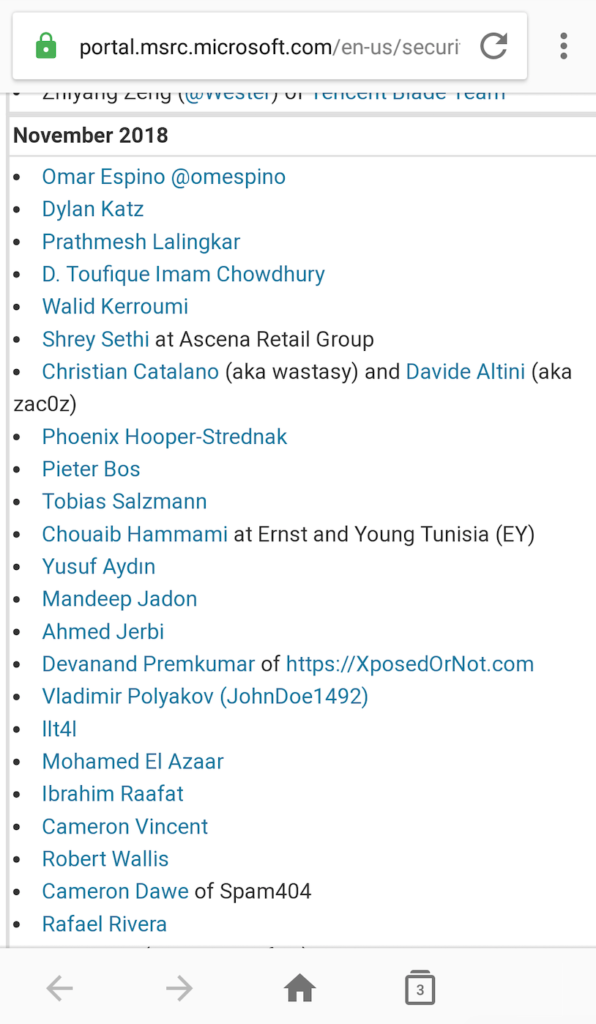
Microsoft HOF (November 2018):
Report Timeline
21 Feb 2018: Sent the report to secure@microsoft.com
21 Feb 2018: Got confirmation from Microsoft team and team begin the investigation
23 Mar 2018: Microsft team ask for some details
23 Mar 2018: Sent details to Microsoft team
26 Jul 2018: Update from the team that the investingation was still in progress
07 Nov 2018: Update from the team that saying that it appears that the submission qualifies for Bounty
26 Nov 2018: Microsoft Reward paid through their payment system – [Profit]
04 March 2019: Ask for disclose permission
14 March 2019: Disclose permission granted from Microsoft team
well that’s it, share your thoughts, what do you think about how they handle that security issue? if you have any doubt, comments or sugestions just drop me a line here or on Twitter @omespino, read you later.

Great work buddy as always. Thanks for sharing.
Thanks for your thoughts and thanks for reading mate.
Nice finding bro.
Thanks mate
Great Writeup Dude!
cool, thanks for reading
You are amazing
thanks mate and thank you for reading