Introduction:
Hello , here is my write up for the CTF “Desafio ESET #36: Juego de escape criptográfico” (ESET Challenge # 36: Cryptographic escape game)
This blogpost appeared first in the book Bug Bounty Write Ups Collection
CTF:
https://www.welivesecurity.com/la-es/2017/12/26/desafio-eset-36/
CTF Solution (official):
https://www.welivesecurity.com/la-es/2018/01/12/solucion-desafio-eset-36/
Rules:
1.- download the desafio36.zip file (mirror) md5=2b7a11892638179573f7b17c4b74911a
2.- unzip the file
3.- start looking for clues and find the CTF flag.
[disclaimer] if you want to give it a shot, stop right now and try to solve the CTF without seeing the write-up, if you don’t keep reading.
CTF solution:
• unzipping the file and verify what kind of files are those with the command “file”
localh0st:Desktop user$ file desafio36/*
desafio36/algo: PDF document, version 1.6
desafio36/bipbip: RIFF (little-endian) data, WAVE audio, Microsoft PCM, 16 bit, stereo 44100 Hz
desafio36/otro archivo 7z: 7-zip archive data, version 0.4
desafio36/un archivo 7z: 7-zip archive data, version 0.4
• we analized the pdf file “algo” with exiftool y and found 2 interesting things:
the pdf’s Author encoded in base64 “U3RlZmFuIEhldHps” – Stefan Hetzl in plain text and a string with roman numerals (hidden with white font color in the document) “LXVI CXVII XCVIII XCVIII CVIII CI LXVI CXI XCVIII XCVIII CVIII CI”, that translated from roman numerals to decimal throws “66 117 98 98 108 101 66 111 98 98 108 101” and the decimal to ASCII give us the string “BubbleBobble”
searching on google i found a program create by Stefan Hetzl steghide – Steghide is a steganography program that is able to hide data in various kinds of image- and audio-files. (JPGE , WAV, BMP, etc..) , so we have a WAV file called “bipbip”, so we tried with “BubbleBobble” password:
steghide extract -sf desafio36/bipbip -p "BubbleBobble"
# and we can extract a file called "mensaje.txt" with another base64 string enconded
localh0st:Desktop user$ cat "mensaje.txt"
S25haHQgdW95IE9pcmFtISBUdWIgcnVvIFNzZWNuaXJwIHNpIG5pIHJlaHRvbmEgZWx0c2FjIQ
localh0st:Desktop user$ cat "mensaje.txt" | base64 --decode; echo
Knaht uoy Oiram! Tub ruo Ssecnirp si ni rehtona eltsac!
my first impression was that the text was reversed, so I tried to use it as a password for the 7z files but it doesn’t work, then I reversed each word to get the Super Mario bros bummer phrase
Thank you Mario! But our Princess is in another castle! (the “otro archivo.7z” 7zip file password)
• analyzing the “otro archivo.7z” file:
we unzip the file and get the “imagen.bmp” file , an “Hackerman” image with two curious coloreds lines in the top and the bottom, and we extracted the hexa notation color from each color and we found a pattern “21726b 72697a 672065 6c2069 766a20 666976 7a6c68 2070a1 202c75 66666e 677676 69794b 20796a 6c6973 706c58 206664 726363 207644” that translated from hex to ASCII give us the string “!rkrizg el ivj fivzlh p¡ ,uffngvviyK yjlisplX fdrcc vD”, so the hint was that the last letter was in upper case so we reversed the string
localh0st:desafio36 user$ echo '!rkrizg el ivj fivzlh p¡ ,uffngvviyK yjlisplX fdrcc vD' | rev
Dv ccrdf Xlpsiljy Kyivvgnffu, ¡p hlzvif jvi le gzirkr!
Cesar cipher? might be, so we tried with a cesar cipher calculator and bingo, with English alphabet and ROT9 we were able to obtain:
Me llamo Guybrush Threepwood, ¡y quiero ser un pirata! (the “un archivo 7z” 7zip file password – in English “My name is Guybrush Threepwood, and I want to be a pirate!”)
• analyzing the “un archivo.7z” file:
after unzip we get the “video.mp4” file, we play the video and it seems like STAR WARS tribute, and in the end, shows up another base64 encoded “flag” that we decode
localh0st:downloads user$ echo rwwgy2ftaw5vignvbwllbnphigvuigxvcybtzxrhzgf0b3mu | base64 --decode
El camino comienza en los metadatos.
#(in english "the way is in the metadata"), so again analize with exiftool
localh0st:desafio36 user$ exiftool ~/Downloads/desafio36/video.mp4 | egrep 'URL|Encoded'
Promotion URL : : ( 10111000 10001101 10001010 10010001 10011011 10001100 10001011 10011010 10010011 10010011 10001010 10010001 10011000 11000101 11011111 10111000 11011111 10101011 11011111 10111110 11011111 11010000 11010000 11011111 10101101 10010110 10010001 10011000 10001100 10001011 10011010 10010011 10010011 10001010 10010001 10011000 11000101 11011111 10111110 11011111 10111110 11011111 10111110 11011111 11010000 11010000 11011111 10101000 10011110 10010011 10000101 10011010 10010001 10010011 10011110 10011000 10011010 11000101 11011111 11001011 11011111 11001101 11011111 11001010 11011111 11010000 11010000 11011111 10101100 10001011 10011010 10011100 10010100 10011010 10001101 10011101 10001101 10011010 10001011 10001011 11000101 11011111 10111011 10110000 11011111 10110001 10110100 11011111 10111010 10100110
Encoded By : Base64
Author URL : https://www.welivesecurity.com/la-es/2016/11/30/criptografia-mainstream/Author URL tag is a clue from an ESET LA blog that is about cryptography.
this was very tricky, after some hours of thinking, I tried with a lot of encodings but at the end I thought, what if the numbers are inverted? and yes, they were, so after changing the 0's for 1's and vice versa bingo! german words (enigma machine, maybe?):
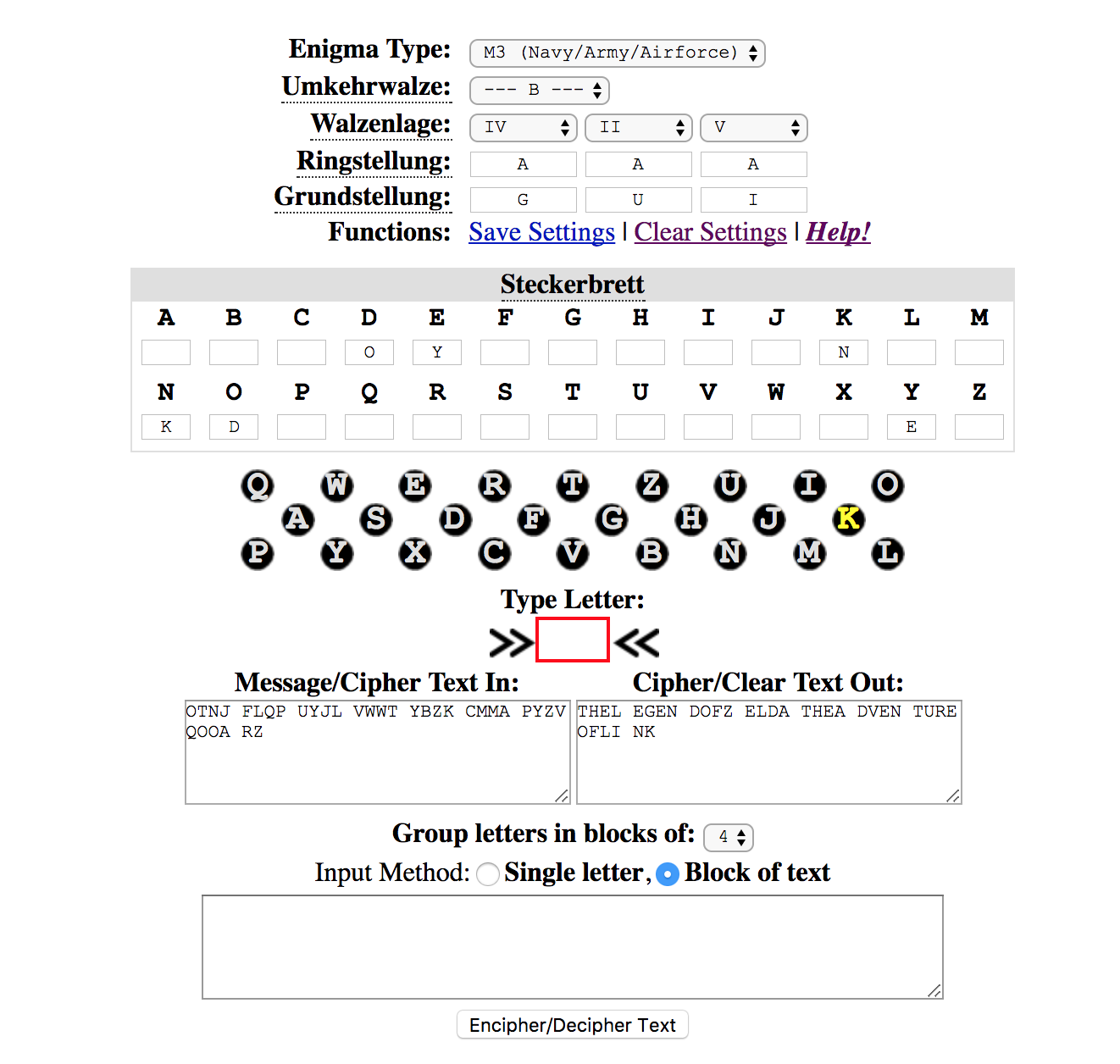
Grundstellung: G T A // Ringstellung: A A A // Walzenlage: 4 2 5 // Steckerbrett: DO NK EY
• analyzing the “bipbip" file again:
I got stuck again, so after some hours of thinking again, listening to the bipbip file again I noticed something weird, it sounds like a bips and claps that apparently does not make any sense, but I decided to open the file with Aegisub and see the audio spectrum and there was like a dots and vertical lines, dot, and lines? of course, the MORSE code
___ _ _. .___ .._. ._.. __._ .__. .._ _.__ .___ ._.. ..._ .__ .__ _ _.__ _... __.. _._ _._. __ __ ._ .__. _.__ __.. ..._ __._ ___ ___ ._ ._. __..
that decoded to text shows up the string
OTNJFLQPUYJLVWWTYBZKCMMAPYZVQOOARZ (enigma machine again?) so, i tried with a enigma machine emulator and the keys and bingo
“THEL EGEN DOFZ ELDA THEA DVEN TURE OFLI NK” (my favorite NES game btw)
I got stuck again, after almost one day, I read my write up the draft, maybe I was missing something, most of the files was analyzed, maybe one file has another hidden secret I thought, and after reviewing my draft step by step, I saw something vital that I was missed before in the steghide documentation
“The JPEG, >>>>>> BMP <<<<<<, WAV and AU file formats are supported for use as cover file”
• analyzing the “imagen.bmp” file again:
BMP? the image of “HACKERMAN” was actually a BMP file the “imagen.bmp”, and after some tries, yes! we were able to extract another file called “mensaje.txt”
localh0st:Desktop user$ steghide extract -sf "imagen.bmp" -p "THELEGENDOFZELDATHEADVENTUREOFLINK"
# wrote extracted data to "mensaje.txt"
• analyzing the other “mensaje.txt” file :
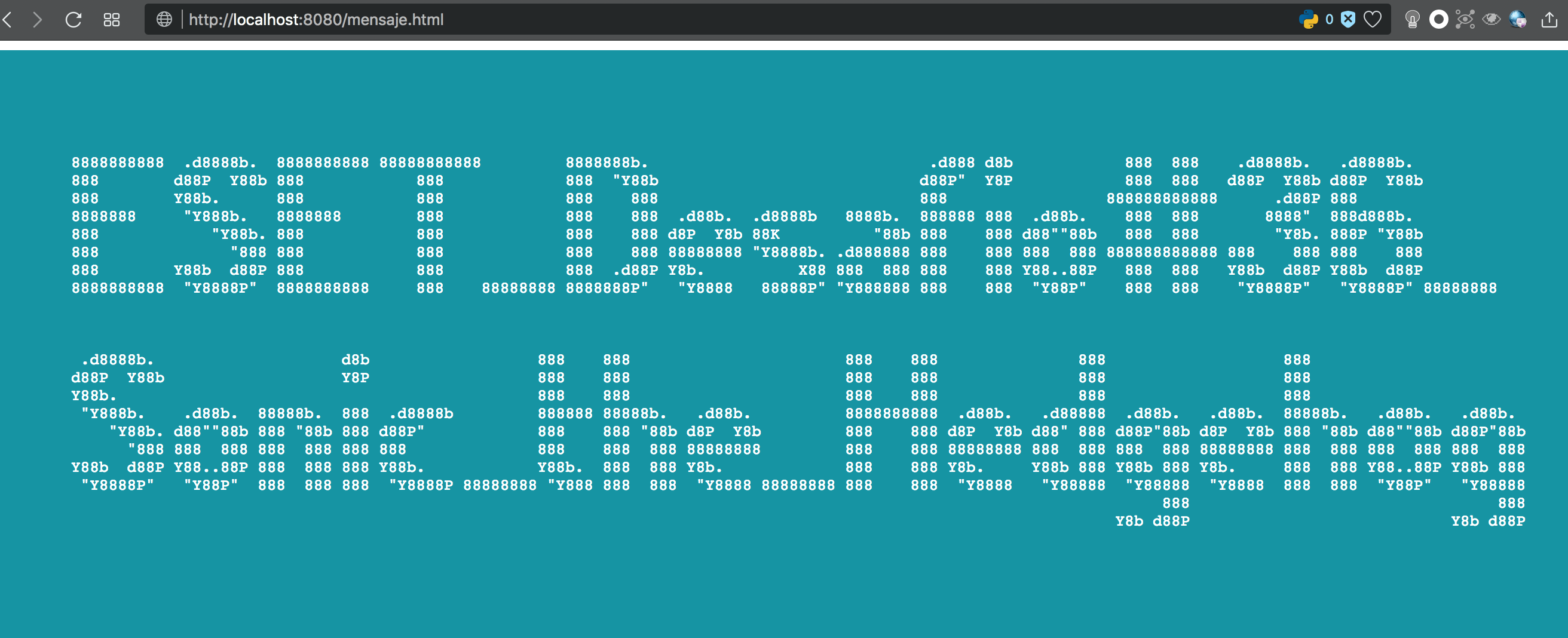
a new file with javascript code apparently, so we rename the mensaje.txt file to mensaje.html, and added the respectively the scripts tags, and with a terminal, I started an HTTP static server in the mensaje.html folder (in this case with python 2.7, with the SimpleHTTPServer module)
localh0st:Desktop user$ python -m SimpleHTTPServer 8080 &we open the browser and navigate to localhost:8080/mensaje.html and BOOOM!, a blue webpage with white letters with the beautiful FLAG
FLAG "ESET_Desafio#36_Sonic_the_Hedgehog"I must say that it cost me a lot, much as I thought actually but I learned some new stuff, but overall this was very fun (and I won a ESET Internet Security License).
well, that’s it, if you have any doubt, comments or suggestions just drop me a line here or on Twitter @omespino, read you later.