Introduction:
Hi everyone It’s been a while since my last post but I’m back, I want to tell you a very short story about one of my last bugs, and how I managed to get an Arbitrary local macOS file read via <a> tag and null byte (%00) in Google Earth Pro Desktop app
This blogpost appeared first in the book Bug Bounty Write Ups Collection
Extracted from Google VRP’s report: (the actual Google VRP report)
Summary: Arbitrary local file read (macOS) via <a> and null byte (%00) element in Google Earth Pro Desktop app
Steps to reproduce:
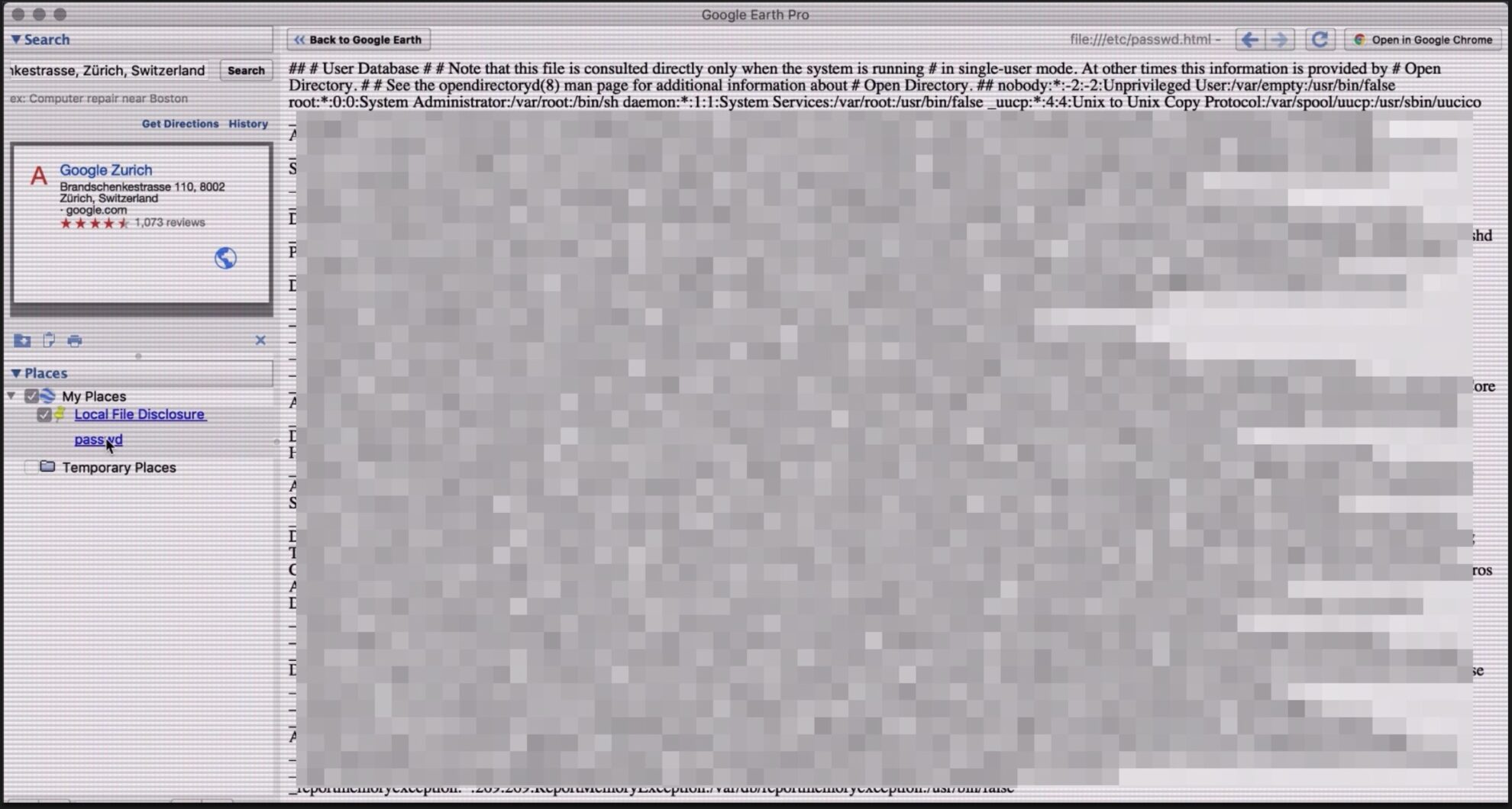
1.- Download and install the latest Google Earth Pro Desktop app for macOS (7.3.3.7786 64-bit)
2.- Open the Google Earth app and create a new Pin, add any name add click on add link, and paste this code in the white box<a href="file:///etc/passwd%00.html">passwd</a>
and click OK button
3.- After Pin’s creation, in the left side pane Places, click in the hyperlink called passwd add see /etc/passwd file content
4.- Profit
PS. any attacker can read any file with file:/// schema and appending a null byte and dot HTML extension (%00.html)
Attack scenario
Any attacker can read arbitrary files on macOS through the Google Earth Pro Desktop app
Report Timeline:
Apr 17, 2021: Sent the report to Google VRP
Apr 19, 2021:  Nice catch! Bug Accepted (P4 → P2)
Nice catch! Bug Accepted (P4 → P2)
Apr 27, 2021: Got a message from Google that the issue does not meet the bar for a financial reward
May 05, 2021: Got a message from Google that the issue report has been closed without providing a fix (Status Won’t fix)
Well that’s it, share your thoughts, what do you think about how they handle that security issue? If you have any doubt, comments or suggestions just drop me a line here or on Twitter @omespino, read you later.