Introduction:
Hi everyone FINALLY I get into Facebook Whitehat Program Hall of Fame After 9 tries, this is my 2nd bug bounty and my very first write up, so here we go:
This blogpost appeared first in the book Bug Bounty Write Ups Collection
Vulnerability Scope: Main Site (www.facebook.com)
Status: Mitigated
Title: “Getting access to prompt debug dialog and serialized tool on main website facebook.com”
Product / URL: www.facebook.com
Description and Impact:
Hi Facebook sec team, I was trying to enumerate some Instagram subdomains (domained) when I found that the following subdomain list, I just pick up one, opened in the browser and logged in the “facebook login” and the login take me to the “main” facebook.com page and shows some debugs prompts and some tools / and missing dependencies while I was scrolling in the new feeds.
Impact:
Nobody outside of the facebook team should be able to see any debug information any attacker can take a leverage and get confidential information about facebook.com website source code, intellectual property or even worst see facebook with developer permissions.
Reproduction Instructions / Proof of Concept:
1.- Login in whatever domain listed below with your fb credentials (the all subdomains prompts the debug info):
https://en-us.latest.instagram.com/ – Resolved to: X.X.X.X
https://developers.latest.instagram.com/ – Resolved to: X.X.X.X
https://www.latest.instagram.com/ – Resolved to: X.X.X.X
https://en-gb.latest.instagram.com/ – Resolved to: X.X.X.X
[and some another http analog subdomains …]
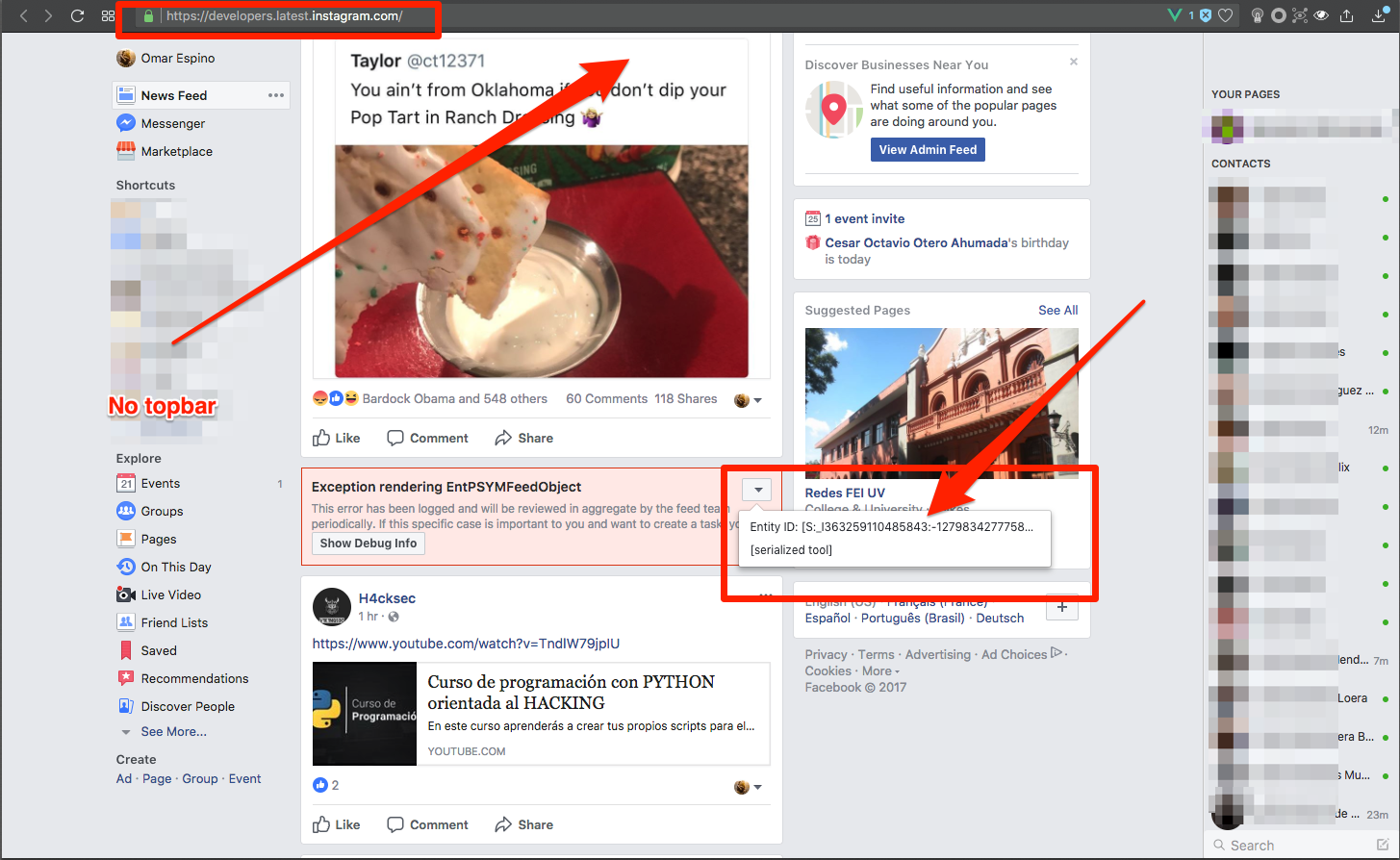
2.-. Scroll to see the new feeds and some exceptions appear with some show debug info on it (the facebook.com website didn’t show the top bar only the “body”, “groups/favorites” panel and the “chat” panel) and some weird debug prompts:
Exception rendering EntVideoCreationStory:
This error has been logged and will be reviewd in aggregate by the feed team periodically, If this specific case is important to you and wan to create a task, you can
(button) Show Debug info
Invalid URI: /ads/about
and this exception
Exception rendering EntPSYMFeedObject:
This error has been logged and will be reviewed in aggregate by the feed team periodically, If this specific case is important to you and wan to create a task, you can
(button) Show Debug info
Invalid URI: /ads/about
but this last also let me show a tiny menu with 2 elements:
Entity ID: [S:_XXXXXXXXXXXXx:-XXXXXXXXX…]
[serialized tool]
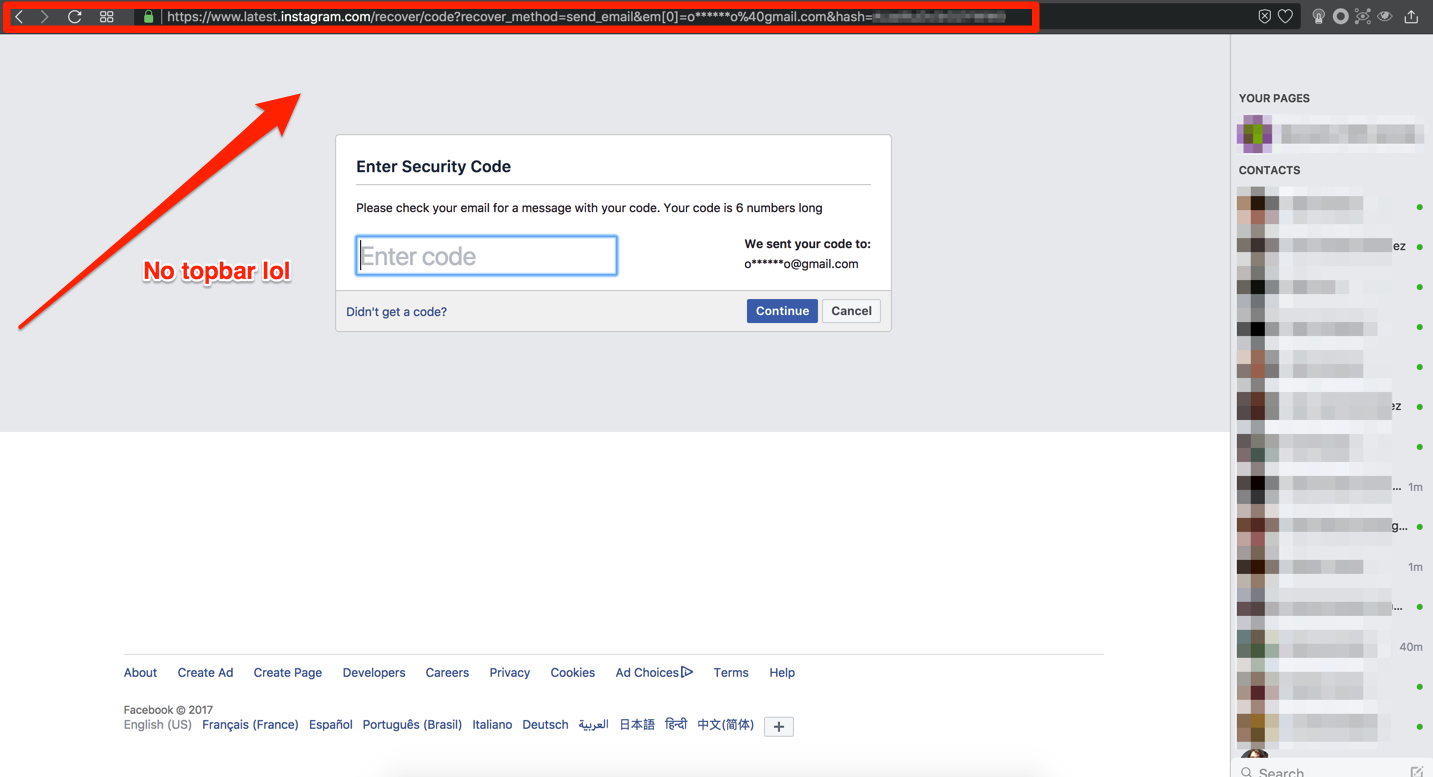
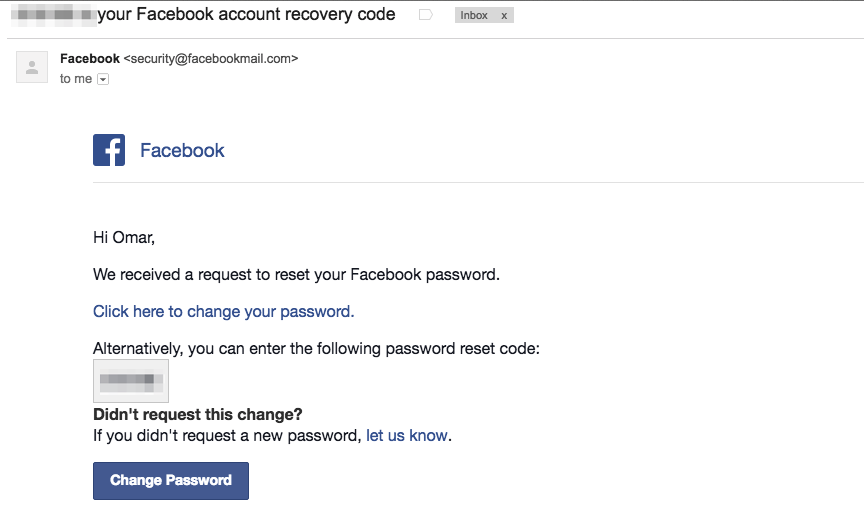
3.- Try to play with some endpoints (per ex. https://www.latest.instagram.com/recover/initiate?lwv=110) and I was able to try to recover my password with and endpoint with a session loaded broken and even received the email to recover the password
4.- Open my fb profile https://www.latest.instagram.com/omespino, open the browser developer tools and see the console, and shows missing dependencies called RoyalBluebar and ButtonGroup monitor.
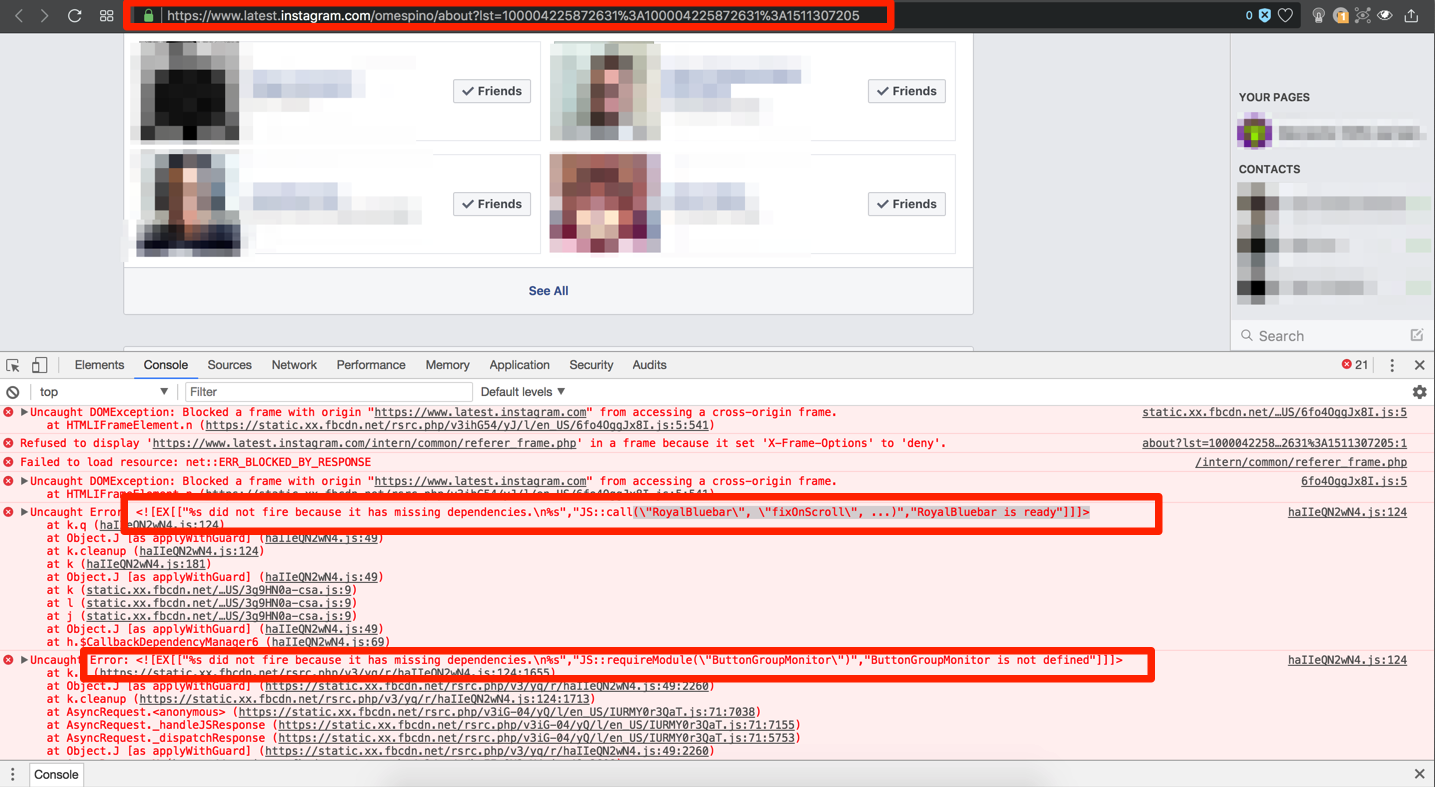
5. – I setup a simple proxy (burpsuite) to see the navigation history and I apparently I have found an endpoint that had the debug options activated
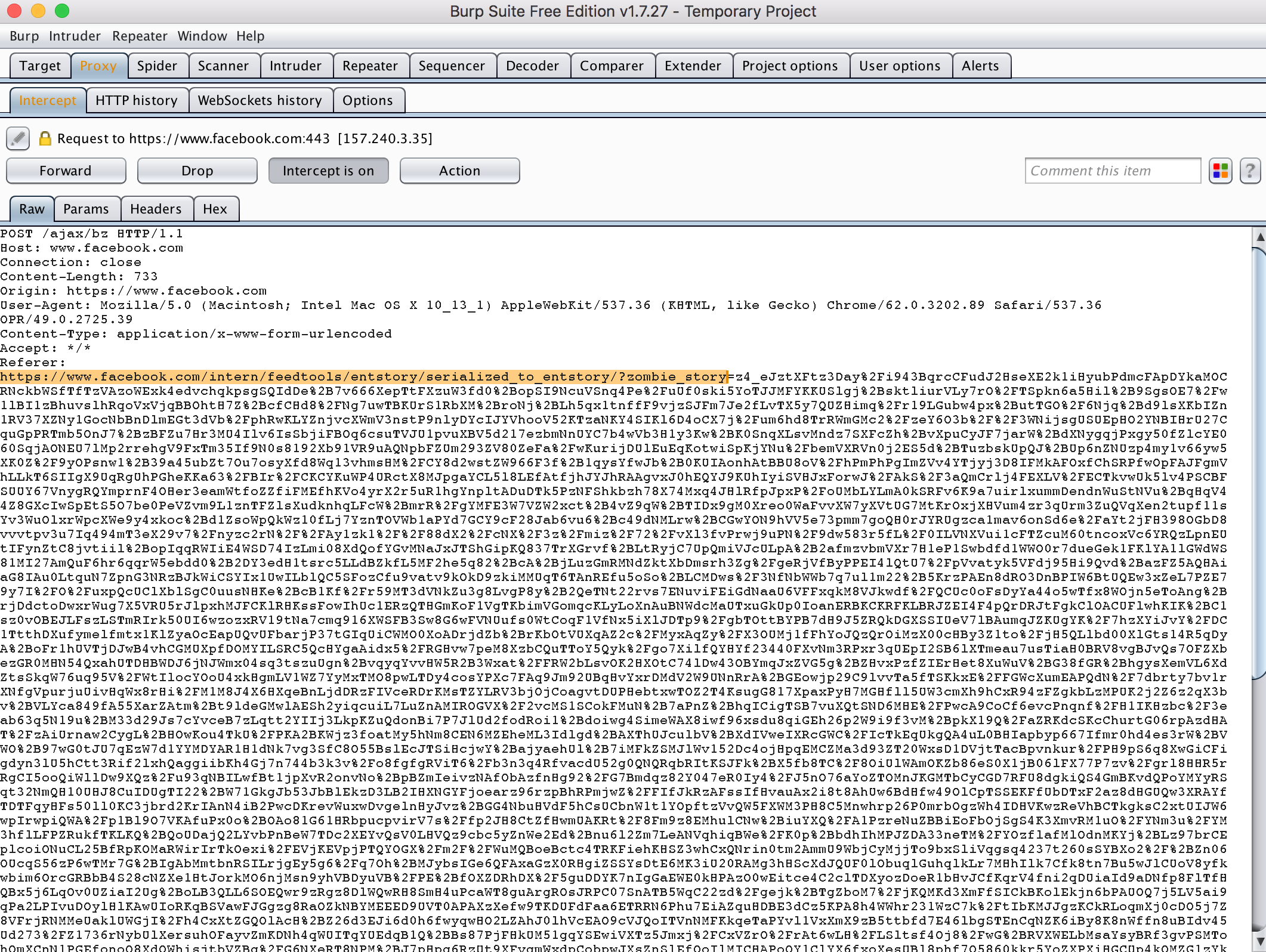
6.- Once I saw that information I destroyed the all sessions and logged out “developer mode” and I didn’t dig more in the bug.
My Assumptions (correct me if I am wrong in the comments please):
Most “modern” application works with routers or main files that control the application workflow (per example: index, router), the bug behavior is quite simple in some scenarios like:
When in some app (PHP app per sample) the main file needs some server variables to work properly like:
<?php
echo "http://" . $_SERVER['APP_URL'] . "/" .$_SERVER['REQUEST_URI'];
?>So, if you access to http://facebook.com/home.php output will be like:
"http://" . "facebook.com" . "/" . "home.php"Note It might apply with some vars like $_SERVER[‘SERVER_NAME’] or $_SERVER[‘HTTP_HOST’]
If we take my POC example http://developers.latest.instagram.com/home.php output will be like:
"http://" . "developers.latest.instagram.com" . "/" . "home.php"
and consequently there will be a prompt error saying that the file “home.php” is not reachable and might show more information to try the solve the problem because the application is at “development” environment. (It seems like it is a sort of like Host Header Attack)
Summarizing , if you have some subdomain pointing to one server that have different domain (subdomain in this case) that the [ server name / base url / app url / host ] the application will be crash trying to get files that aren’t even exist on that server leaking information that you don’t want to.
Timeline:
21 Nov 2017: Initial report
22 Nov 2017: Security team member Linda ask if I can see the full stack trace exception
22 Nov 2017: I replied Linda by sending screenshot that shows additional info
25 Nov 2017: Bug acknowledged and Neal said that fix is in the progress
11 Dec 2017: Neal informed me that vulnerability has been mitigated but still have work to do.
12 Dec 2017: I replied confirming that the bug was patched
20 Dic 2017: Facebook Reward paid through Bugcrowd payment system – [Profit]
20 Dec 2017: I asked about disclosure
31 Jan 2018: Disclosure approved.
well, that’s it if you have any doubt, comments or suggestions just drop me a line here or on Twitter @omespino, read you later.

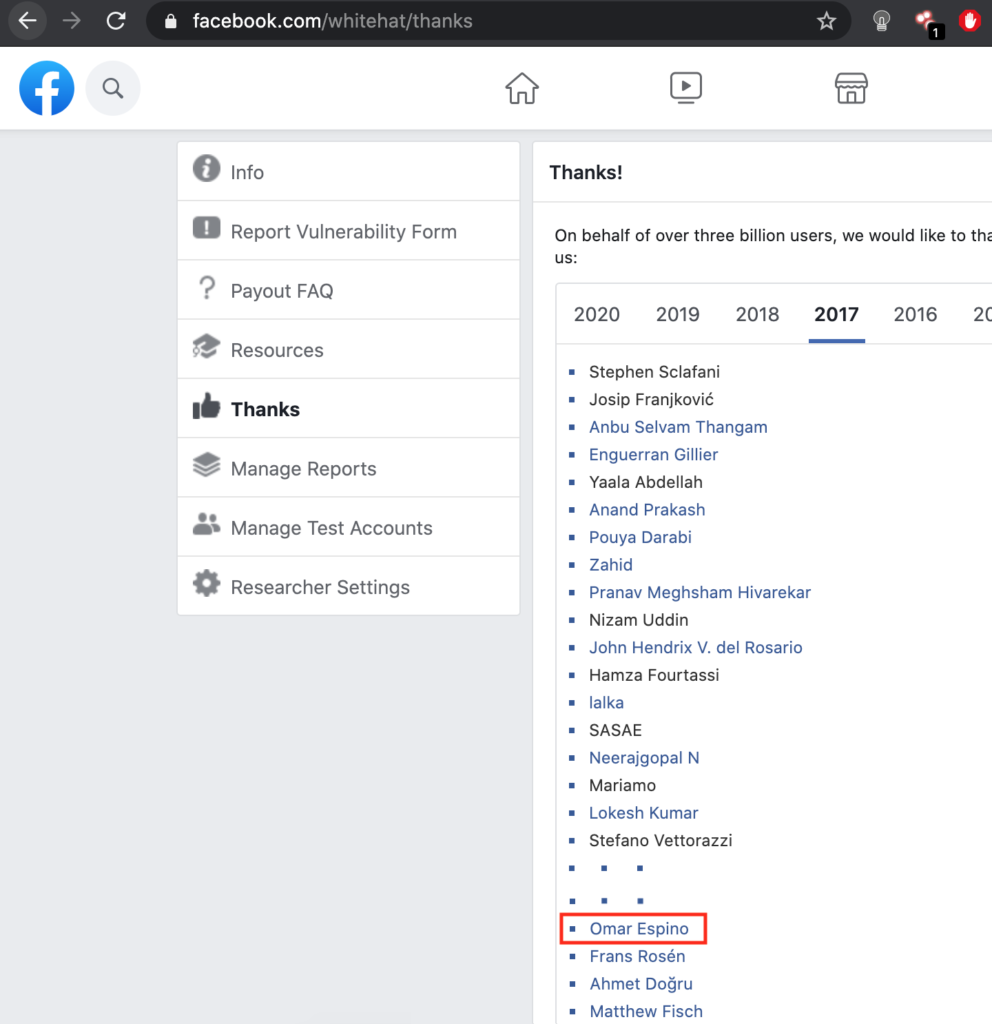
Creat find, mate!
BTW what tool you use for scanning subdomain??
thanks for reading, the tool is called domained here is the source https://github.com/reconned/domained.
Great find
Thanks mate.
how do you recon ??
the tool is called domained here is the source https://github.com/reconned/domained
Make a more new posts please 🙂
___
Sanny
Thanks for your enthusiasm , for sure my plan is update more often the blog
Hey, I think yourr website might be having browser compatibility issues.
When I look at your blog site in Opera, it looks fine but when opning in Intesrnet Explorer,
it hass some overlapping. I just wanted to give yoou a quick heads up!
Other then that, excellent blog!
Hey thanks for pointing this out, and you know, Internet Explorer …, anyway I’ll take a look, thanks for reading mate