Introduction:
Hi everyone It’s been a while since my last post but I’m back, now I want to show you that you can start hacking android apps with frida without pain, I took me several hours to figure out how to get the frida installation ready but at the end that wasn’t really really difficult, the main problem is that I didn’t found a pretty clear tutorial for beginners in mobile security like me, so that’s why decided to create this 10 min tutorial. if you want to skip frida description you can go directly to Step 0 to start frida installation
This blogpost appeared first in the book Bug Bounty Write Ups Collection
So what is frida, exactly?
Extracted from frida website:
“It’s Greasemonkey for native apps, or, put in more technical terms, it’s a dynamic code instrumentation toolkit. It lets you inject snippets of JavaScript or your own library into native apps on Windows, macOS, GNU/Linux, iOS, Android, and QNX. Frida also provides you with some simple tools built on top of the Frida API. These can be used as-is, tweaked to your needs, or serve as examples of how to use the API.”
So basically frida is a tool that let you inject scripts to native apps (in this case Android apps) to modify the application behavoir (in this case make a ssl pinning bypass and can perform a MitM attack, even if the aplication has https / ssl connections) and make dynamic test in real time.
Disclaimer: this method won’t work with applications that uses HSTS (HTTP Strict Transport Security) per example facebook, instagram, twitter, paypal, banking apps, etc, but don’t worry most applications don’t uses this protocol yet.
Step 0 – set up the enviroment
computer
– python 2.7
– pip for python
– adb tools (Android Debug Bridge tools)
– local proxy (Burpsuite by Larry_lau, just kidding Burpsuite comunnity edition)
android phone
– android device rooted (in my case oneplus one with android 8.1) or
– android emulator with android 4.4.4 to 8.1
Step 1 – install frida on your computer
# installing frida via terminal, sometimes you need to run this command as sudo
pip install frida-toolsStep 2 – install frida-server on your device
Since there are a lot kind of android devices arquitechtures we need to find out what processor have our device so we need to connect our device to the computer (with usb debugger option activated) and then run this following command:
# getting the processor arquitecture in this case is ARM, there are also x86, x86_64, etc ...
adb shell getprop ro.product.cpu.abi
ouput: armeabi-v7awell, after know the arch now we can download the properly frida-server version for our device, in this case frida-server-XX.X.X-android-arm in this frida github releases link (since the lastest version didn’t work I highly recommend download this version frida-server-12.0.5-android-arm.xz, anyway you can try with newer version if you want to), once is downloaded we need to extract the frida server and then copy it to the device
# extracting frida-server binary from the xz file
# for linux distributions
tar -xJf frida-server-12.0.5-android-arm.xz
# for macOS or BSD based
unxz frida-server-12.0.5-android-arm.xz
# then we need to copy the frida-server binary to the device with adb
adb push ./frida-server-12.0.5-android-arm /data/local/tmp/Step 3 – Hello process in frida (frida’s Hello world)
Once we have installed frida(computer) and frida-server (android) we can start interacting with frida with the following commands:
# first we need to start frida-server with this adb command
# the last '&' is to run the command in background
# disable SELinux is very important I was looking about 4 hours trying to see what happened and SELinux was preventing the success frida-server execution, also frida-server must run as root
adb shell 'su -c setenforce 0'
adb shell 'su -c /data/local/tmp/frida-server-12.0.5-android-arm &'
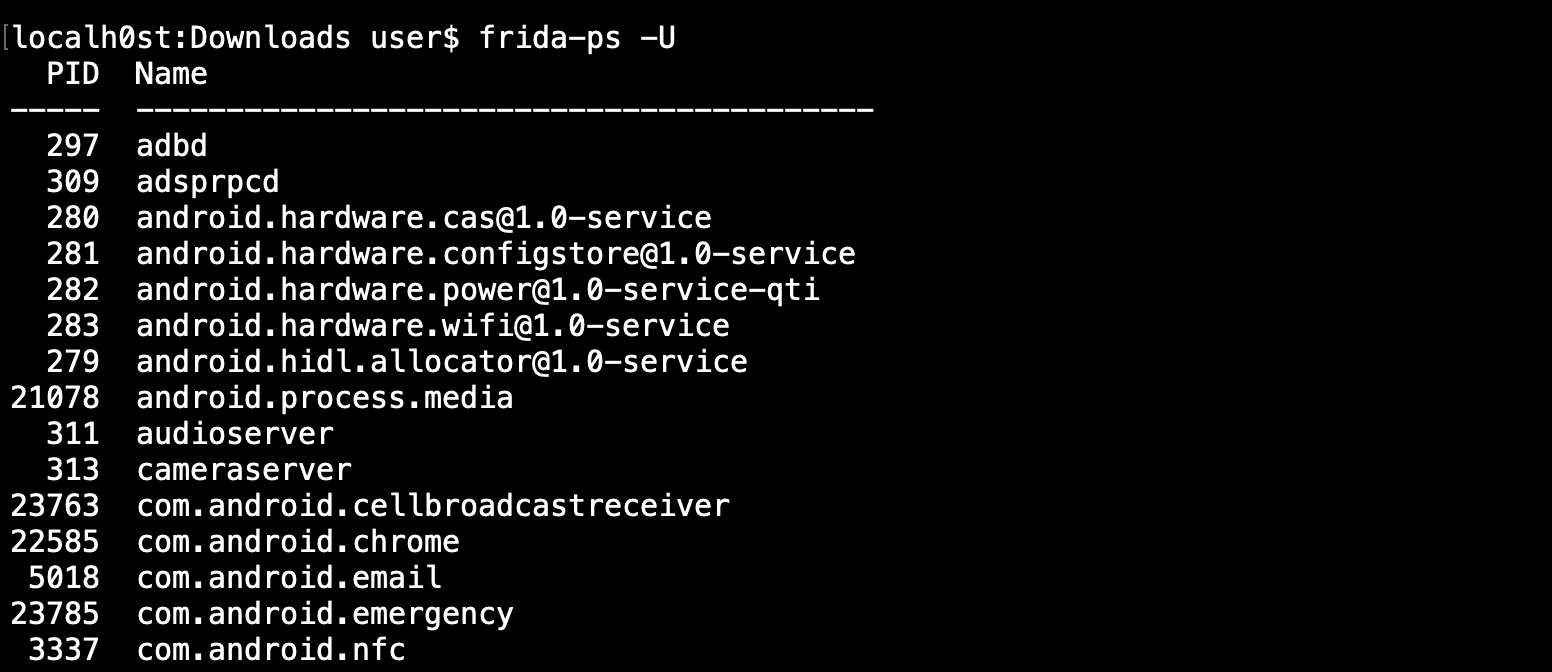
# then if everything works you can see frida's hello world with
# frida-ps is for list the devices process and -U flag is for usb devices
frida-ps -U
Step 5 – Set up Burpsuite comunnity edition
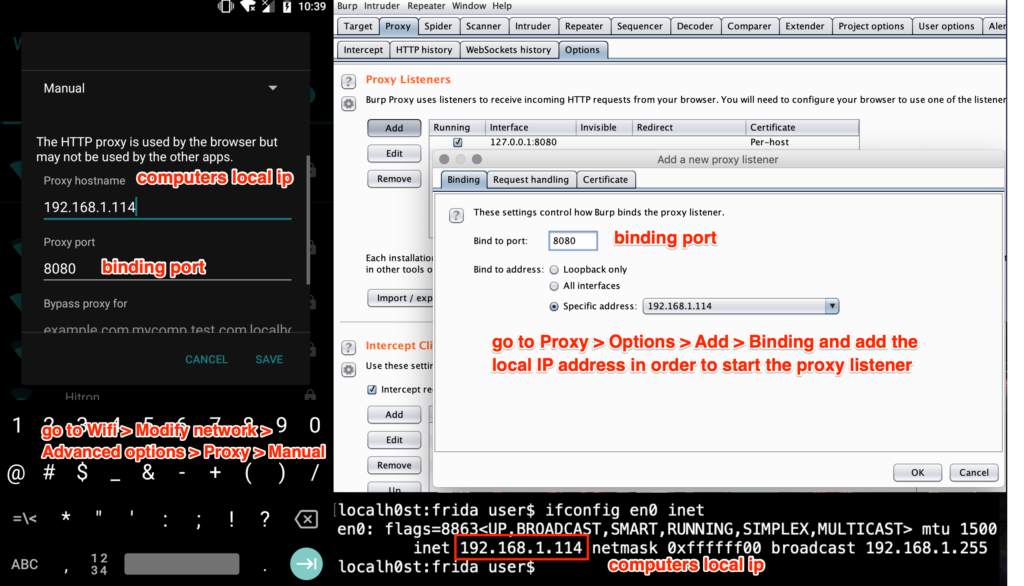
The quickiest way to setup a connection between our devices is get connected the android device and computer in the same wifi, so we just need to set up the android wifi connection to manual proxy in advanced section and also set up Burpsuite with the local computer ip (don’t forget use the same port)
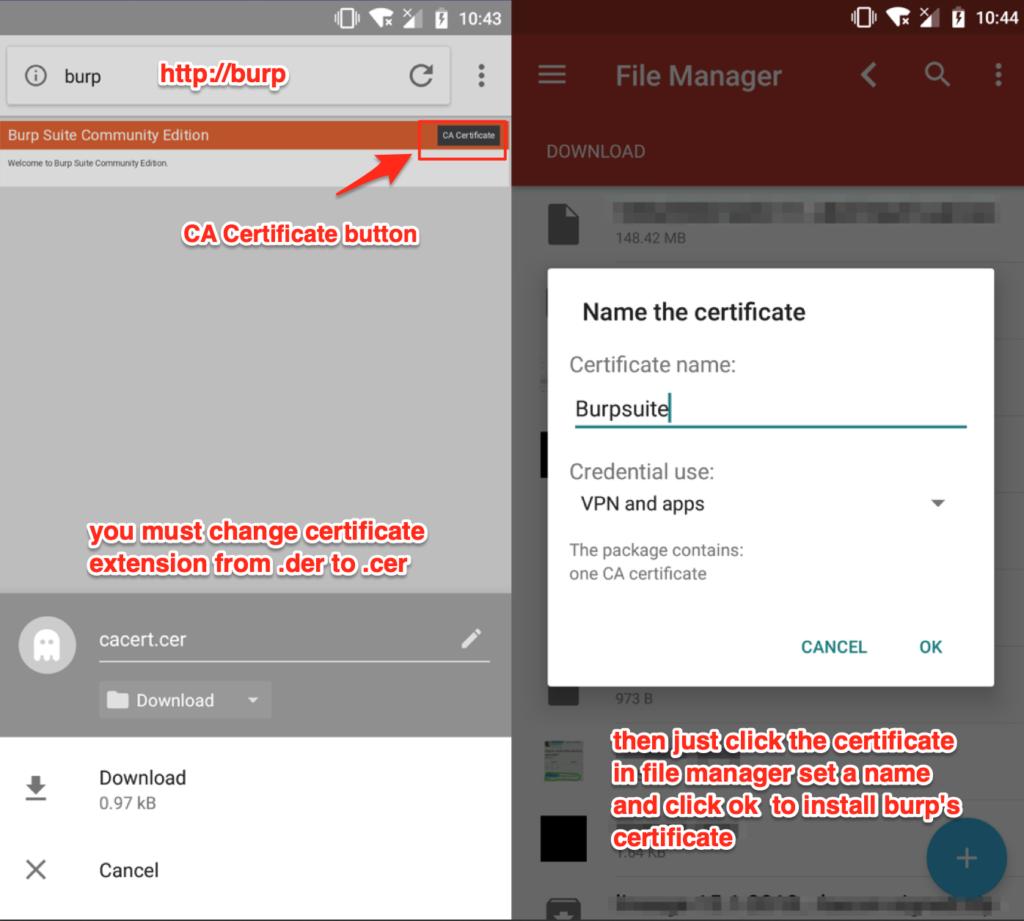
also we need to install the burpsuite certificate, once the android device have the proxy set up we need to access to http://burp in browser, then click the “CA certificate” buton and download the certificate (Note, you need to change the certificate extention from der to cer)
Last step: Bypass SSL pinning with Universal Android SSL Pinning Bypass No.2
So, we got frida, frida-server and burpsuite running as espected, the next step is run the “Universal Android SSL Pinning Bypass No.2” script in order to start sniffing the application connections so we need to get the script and saved locally as name_script.js, here is a blogpost about this script by Mattia Vinci (you can add several scripts to frida from the repo or custom scripts too)
/*
Universal Android SSL Pinning Bypass
by Mattia Vinci and Maurizio Agazzini
$ frida -U -f org.package.name -l universal-ssl-check-bypass.js --no-pause
https://techblog.mediaservice.net/2018/11/universal-android-ssl-check-bypass-2/
*/
Java.perform(function() {
var array_list = Java.use("java.util.ArrayList");
var ApiClient = Java.use('com.android.org.conscrypt.TrustManagerImpl');
ApiClient.checkTrustedRecursive.implementation = function(a1, a2, a3, a4, a5, a6) {
// console.log('Bypassing SSL Pinning');
var k = array_list.$new();
return k;
}
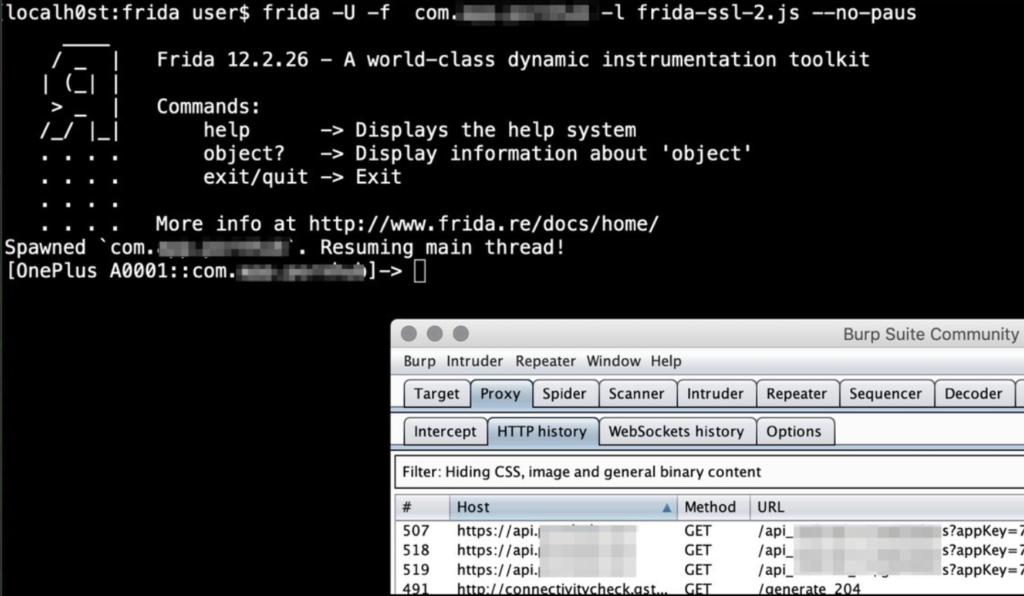
}, 0);so the only thing that we have to do is save this script as “frida-ssl-2.js” and run the following command:
# the -l flag is to run custom script, in this case ssl pinning 2 script
# the -f flag is for the apk package name, --no-paus option to not interrupt
# the app startup at all and still leave the spawning of the process to Frida.
frida -U -l frida-ssl-2.js --no-paus -f com.example.applicationthen the application is going start you are going to see the results in burpsuite
so at this point you successfully bypass the ssl pinning with frida and you can start hacking network connections on android aplications
References:
http://asvid.github.io/android-frida-hackinghttps://koz.io/using-frida-on-android-without-root/
https://www.codemetrix.net/hacking-android-apps-with-frida-1/
https://www.notsosecure.com/pentesting-android-apps-using-frida/
https://android.jlelse.eu/hacking-android-app-with-frida-a85516f4f8b7
well, that’s it if you have any thoughts, doubts, comments or suggestions just drop me a line here or on Twitter @omespino, read you later.

Great post and thanks for the info.
It’s works.
you’re welcome mate, and thank you for the confirmation, neat
Hey Bro, you tutorial is amazing. But i am getting error if i am running this command
adb shell ‘su -c /data/local/tmp/frida-server-12.0.5-android-x86 &’
I am running this on my windows using android emulator. Could you please tell me the solution for the same.
you’re welcome mate, what kind of error? most probably issue is that maybe the device can’t find the “su” binary because is not rooted
Did you check whether your emulator is arm or x86? Use the suitable package of frida-server.
Nice post ! Thanks for sharing bro !
I was create the command mobile pentest cheatsheet, https://github.com/mirfansulaiman/Command-Mobile-Penetration-Testing-Cheatsheet/blob/master/Readme.md please feel free to check it out 🙂 if you know another method or technique please let me know 😉
Thanks you 🙂
your’re welcome mate, I’ll definetly check out that cheatsheet, thanks for sharing
frida-ps command was not available for me after installing frida using pip. I had to install frida-tools to get that.
yeah, my bad, is fixed now, thanks for pointing this and thanks for reading
Hi, I was able to run frida on Windows and on Android.
They seem to start communicating, but my mobile resets.
I was not able to set the proxy ip and port on mobile => it does not communicate (cant access burp site to get certificate)
What am I doing wrong?
Hello, you should try using frida server 12.0.5 version, I was having the same problem (phone was reseting) that you mention in your last comment, and that fixed with downgrading frida server version
Hi, now it is working fine with frida_server_12_2_29_android_arm
I did a couple of mistakes.
Hi,
I am using python 2.7 and frida_server_12_2_29_android_arm on Samsung S4 Mini (rooted)
I am getting a exception
=============================
Exception in thread Thread-1:
Traceback (most recent call last):
File “c:\python27\lib\threading.py”, line 801, in __bootstrap_inner
self.run()
File “c:\python27\lib\threading.py”, line 754, in run
self.__target(*self.__args, **self.__kwargs)
File “c:\python27\lib\site-packages\frida_tools\application.py”, line 428, in _run
work()
File “c:\python27\lib\site-packages\frida_tools\application.py”, line 275, in _try_start
self._update_status(“Failed to spawn: %s” % e)
UnicodeDecodeError: ‘ascii’ codec can’t decode byte 0xe2 in position 32: ordinal not in range(128)
Hi, everything working fine!!!
I am able to do a couple of commands using frida injected.
I am using Charles instead of Burp (could not make it works).
But I can not see any app request. What am I missing now?
I was using a rooted device with Android N (Nougat) that does not accept CA Trusted by users.
Thus, I was not able to connect through WiFi.
Now everything is fine.
Here a tutorial => https://blog.ropnop.com/configuring-burp-suite-with-android-nougat/
Neat, pretty cool and thanks for share mate!
C:\Users\Gokhan> frida-ps -U
Failed to enumerate processes: unable to connect to remote frida-server: closed
I get such an error
How can I solve ?
Hello, this means that your computer does not have connectivy with the frida-server process, you can try adb shell in order to make sure that you have connectivy with your phone and then try again the step 3, something to notice is that this method will work only if you run the frida-server as root.
When I run
adb shell ‘su -c setenforce 0’
I receveive the error
setenforce: Needs 1 argument
Hi,
when i run the script i get the following error:
-> TypeError: cannot write property ‘implementation’ of undefined
at [anon] (duk_hobject_props.c:3402)
at [anon] (/repl1.js:10)
at frida/node_modules/frida-java/lib/vm.js:42
at E (frida/node_modules/frida-java/index.js:348)
at frida/node_modules/frida-java/index.js:334
at input:1
Process terminated
Can you help me to fix it please?
Thanks
Hey it seems that the script is not parsed correctly maybe the copy paste or something, you can find a reference here https://github.com/frida/frida/issues/283
the syntax is the same as you have post in this page and it seems correct.
Maybe I have to try with a different Frida version, did you test the script only with Frida version 12.0.5?
TypeError: cannot write property ‘implementation’ of undefined
Hi, what is the solution of this error?
any help will be appreciate
[05:32:57]-[makki@cp]~/Downloads -> tar -xJf frida-server-12.6.11-android-arm64.xz
tar: This does not look like a tar archive
tar: Skipping to next header
tar: A lone zero block at 25
tar: Exiting with failure status due to previous errors
Hey, you need to install xz-utils in ubuntu per example is with “sudo apt-get install xz-utils” and you can extract that *.xz file with “unxz frida-server-12.6.11-android-arm64.xz”, thanks for reading.