Introduction:
Hi everyone, this is very special to me, is the report for my first bug bounty ever! in 2017, so far I’ve found another bugs in platforms like Facebook and Nokia, but this one will always be my favorite because was the 1st one, so I got into Twitter Security Hall of Fame (2017) via Hackerone, so here we go:
This blogpost appeared first in the book Bug Bounty Write Ups Collection
Report Summary:
Hi Twitter Sec team I’ve found that some of your SMTP servers are vulnerable to the POODLE SSLv3 bug
Description and impact:
CVE-2014-3566: The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other products, uses nondeterministic CBC padding, which makes it easier for man-in-the-middle attackers to obtain cleartext data via a padding oracle attack, aka the “POODLE” issue.
Steps To Reproduce:
One day I just was navigating in shodan and I don’t know why I thinked about the smtp servers and the bug bounties, and that made think about which companies have sslv3 activated in production environments (heartbleeed) , so I decided to try with some dorks in shodan (like “org:Twitter” “port:443” “port:25”) when suddendly some wild server appear:
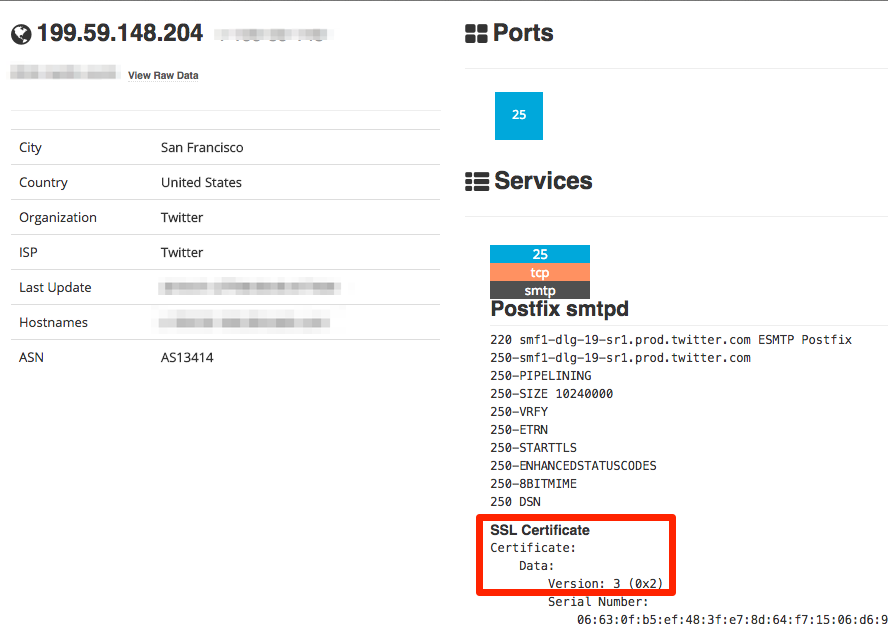
I thought WOW! sslv3 in some Twitter SMTP production server, it was just a matter of time to found more SMTP servers with the sslv3 activated in the same network, once I collected the 4 SMTP servers available (mx3.twitter.com,199.59.148.204,199.16.156.108 and 199.59.148.204), the fun began.
Extracted from the h1 report:
Hi Twitter Sec team here is the POC
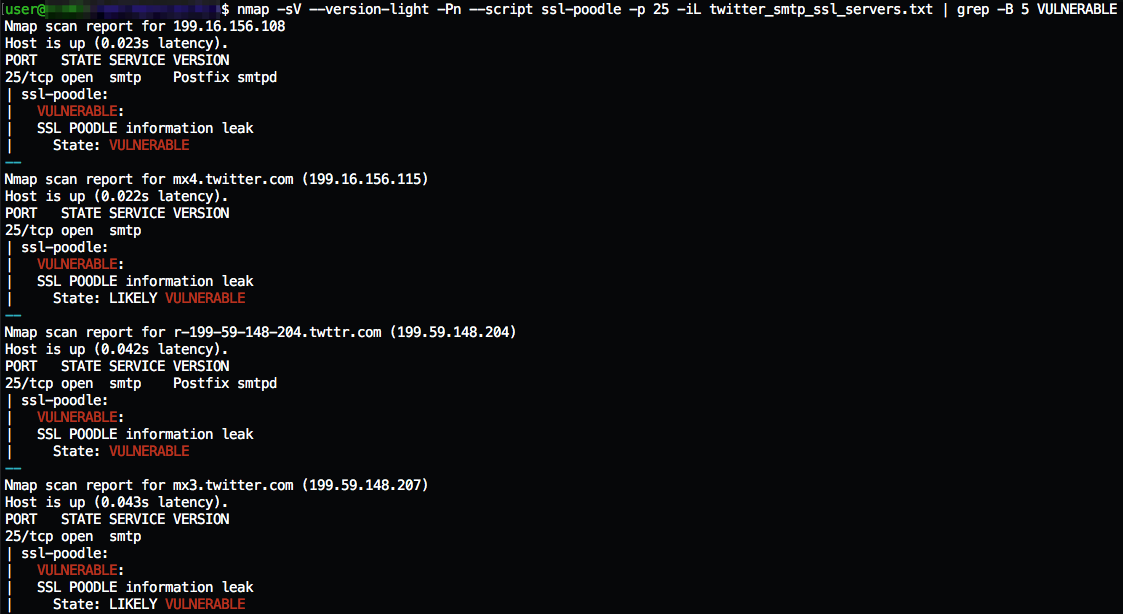
1.- get a nmap installation and twitter_smtp_ssl_servers.txt file (file with mx3.twitter.com,199.59.148.204,199.16.156.108 and 199.59.148.204 hosts row by row)
2.- run this command : “nmap -sV –version-light -Pn –script ssl-poodle -p 25 -iL twitter_smtp_ssl_servers.txt | grep -B 5 VULNERABLE”
3.- And that’s it, see the results
Tools: nmap, grep, shodan.io
Is this bug public or known by third parties? No
Can I reproduce this issue every time? Yes
How did I find this bug? via shodan.
Twitter Hall of fame:
Hackerone report:
well, that’s it, if you have any doubt, comments or suggestions just drop me a line here or on Twitter @omespino, read you later.

Cool find, did you probe further after this or you just stopped here and reported it straight away?
Hey thanks for reading, I just stopped and reported after I founded that servers, the twitter team does not requiered any poc, here is the original report for reference https://hackerone.com/reports/288966
Hi Omespino,
I am trying to use the same dork for Twitter and as well as for other targets, but not getting results.
I am getting “No results Found”